Will Zyxel Nebula survive on the sovereign internet?
We have reviewed the Nebula Control Center management system from Zyxel many times. This is a cloud service that allows you to configure and monitor the company's network stack via the Internet, including setting up Wi-Fi, connecting offices via VPN, and what is most pleasant - it is easy to get out of unpleasant situations when the administrator made a mistake in the LAN settings and the internal network was blocked. Constant access to all devices via WAN, and even in single window mode is a key feature of Nebula Control Center, for which users buy Zyxel equipment. It is especially convenient to configure some remote Edge nodes through Nebula, which the operator can configure without leaving home, through a mobile application on a smartphone. But, this solution has one drawback, which has become more relevant today than ever…
Nebula Control Center is a completely cloud-based solution that works only via the Internet, and unlike TP-Link Omada SDN software controllers (see our article) or Ubiquiti Unifi Controller (see our comparison of Zyxel vs Ubiquiti), there is no option to install control software on a local server or VDS. The days of the free Internet seem to be far in the past, and today the Iron curtain can come down at any moment, turning what we call the global network into something self-contained. What will happen to your network in this case, whether Zyxel will turn into a "brick", and what to do in this case, we will consider in this review.
What we tested? How we tested?
A standard stack was used for testing: Zyxel ATP200 access gateway + PoE switch + access point configured via Nebula Control Center. The pfSense gateway was deployed on the higher-level equipment, which made it possible to arrange its own mini-reserve with its own locks and bypass tunnels. From below, through an access point, ordinary clients with a normal network life were connected: the Internet, VPN, social networks and YouTube.
When testing, I was interested in 2 questions:
- will the company's local network work if the Nebula Control Center turns out to be unavailable?
- and how, in fact, to regain control of the network equipment?
Stop! The most important point is what will happen to my network?
OK, to test the toughest version of the locks, we lower the "iron curtain" on pfSense and block access to the WAN to the Zyxel ATP200 gateway, after which we overload all the Zyxel equipment.
The network continues to work - Wi-Fi SSIDs are active, clients feel as if nothing had happened: local resources are opened, requests are made to the WAN. The Nebula application on the smartphone reports that the access points, gateway and switch have switched to offline mode, but annoying notifications can be turned off.
We open access to the WAN, but block requests to the Nebula servers, after which we overload the equipment. The network is operating normally: both local resources and the Internet are available to customers (more precisely, what is left of it). Management via the app or Nebula CC is not available.
If you set up 2-factor authentication by E-Mail or Captive Portal for Wi-Fi, then these services will play a cruel joke on you, not letting you into Wi-Fi, so if there is a need for additional confirmation of the user's identity, I recommend using 2F-Auth via the Google app on your smartphone (more about setting up 2FA in Zyxel Nebula, read our article).
TOTAL: even if access to servers located in unfriendly countries is disabled,
! ! ! THE NETWORK WILL CONTINUE TO WORK ! ! !
You will have enough time to plan and implement the return of control over the equipment.
And what does it mean to "regain control of network equipment"?
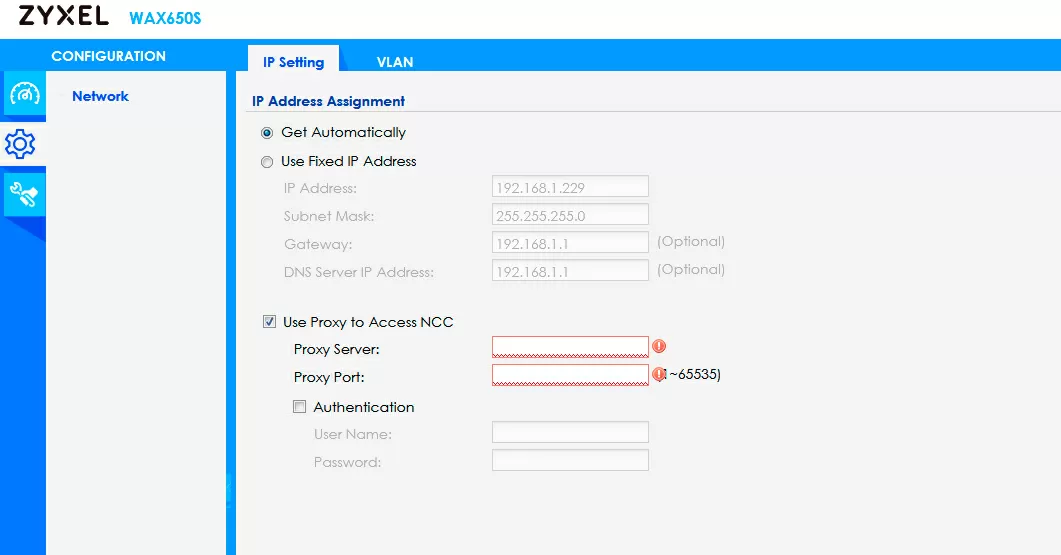
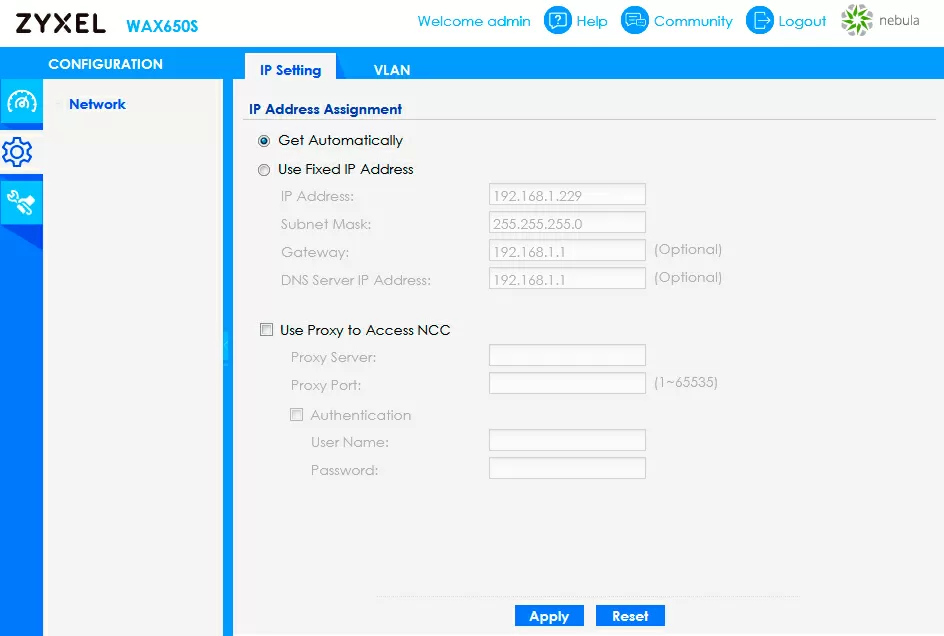
The fact is that Nebula Control Center, when registering a device, completely takes over its management and even changes the password to the WebUI of all devices. The password itself can be found in the "Sites" section of the Nebula interface, and I recommend that you log into your Nebula account right now, while reading this article, and copy the device access password from there to a secure location (Nebula -> Sites -> General Settings -> Device Configurations window).
Even after connecting to Nebula, some devices, for example, switches, leave part of the functions in the Web interface of the device, for example, in switches this is called "hybrid mode", and through WebUI you can configure VLANs, disable ports or overload the device.
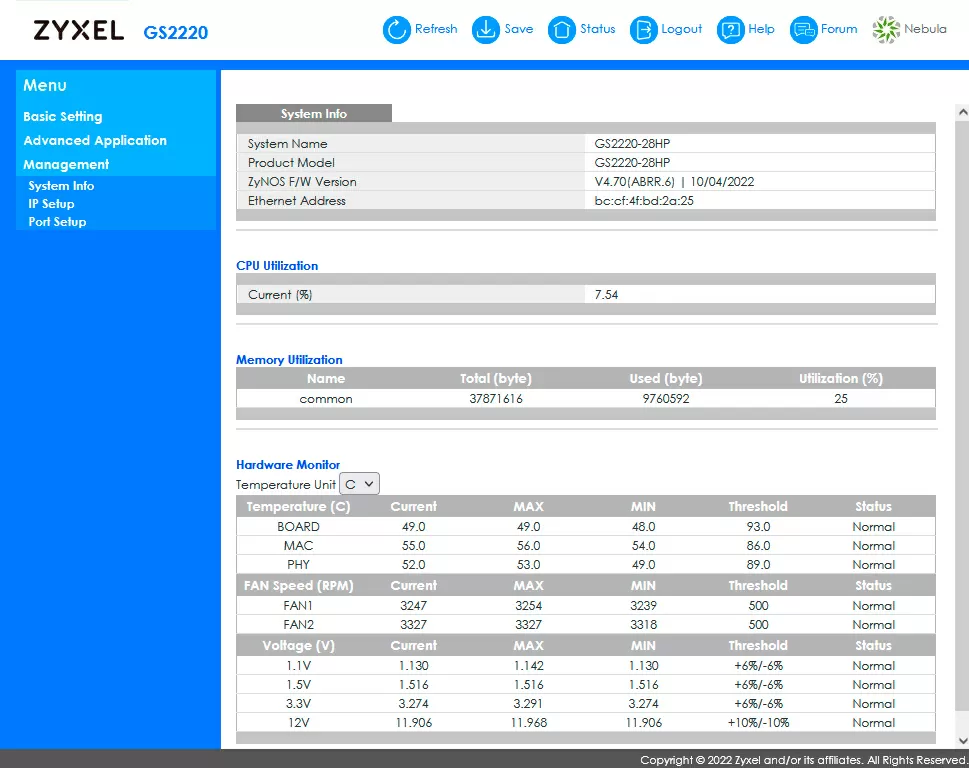
But in order to fully manage network equipment, you need both you and each piece of equipment, be it a gateway, access point or switch, to be able to "reach" the Nebula Control Center servers. But there is also good news: once having received the network configuration from the Nebula Control Center, devices no longer need to have access to this cloud: the configuration is registered locally and loaded from the flash memory of the devices, so the network will continue to work, but it will no longer be possible to manage it or get statistics. However, it is not difficult to regain control of the network equipment.
Difficult option: configure via CLI or SNMP
Advanced system administrators can connect to devices via the command line via SSH or RS-232, or configure via SNMP. You can do this without removing the hardware from Nebula, the interface and command sets are typical here. Another thing is that not every sysadmin is easily given a command line.
Why not just reset the devices to factory settings?
If you reset the device connected to the Nebula Control Center to factory settings, disabling its access to the Nebula servers, then it will boot offline and continue to work in it until it reaches the "cloud". In this case, it will download the configuration and go back under the control of "Nebula". So, this feature can be used to painlessly take your network offline.
For switches, the algorithm is simple: you either need to press the hidden button with a paper clip, or go to the Web interface using the password from the Nebula account (I hope when you read these lines, you have already copied it, as I recommended above) and in the Maintenance tab / Service click "Factory Default". After restarting, go back to the Web UI using the admin/1234 pair and uncheck the Discovery checkbox from the Nebula item in the Cloud Management settings.
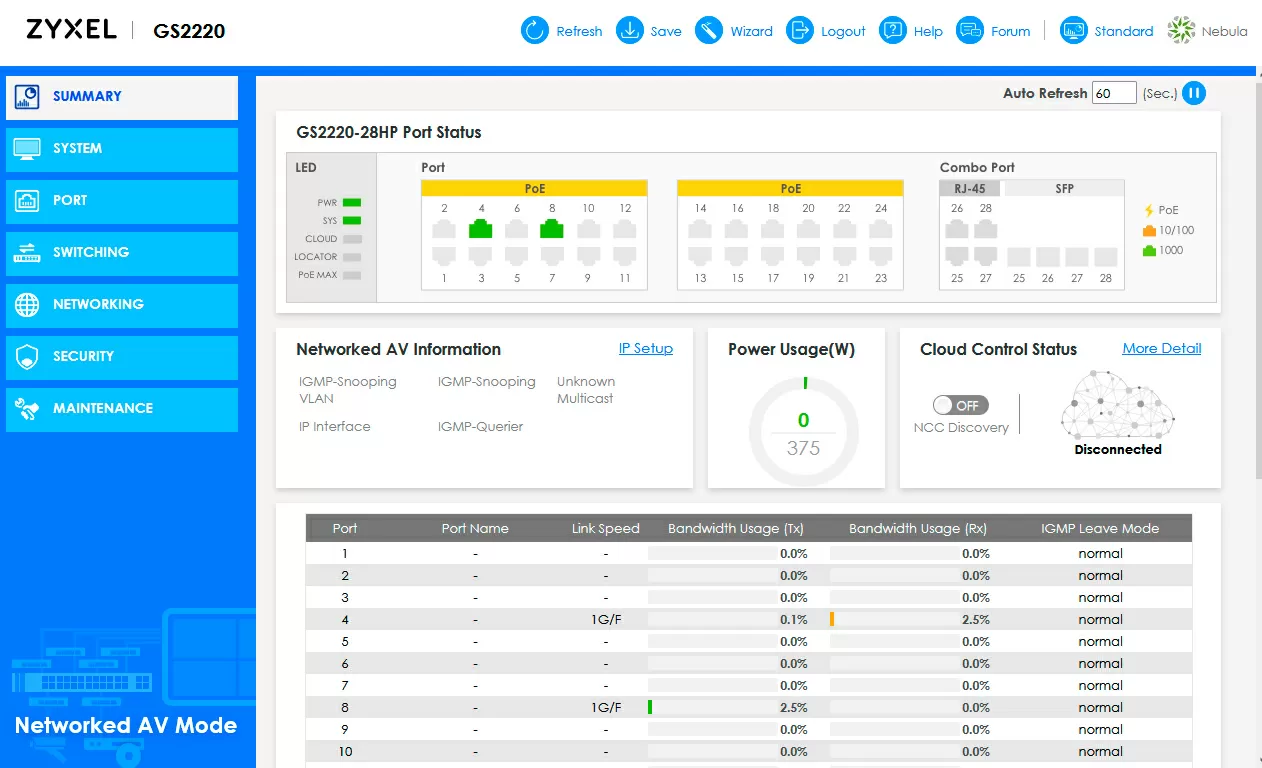
In order not to climb walls and ceilings for hardware reset of access points, it is enough to log in to each of them via SSH with the password that I hope you have finally saved in a safe place and execute the command:
apply /conf/system-default.conf
or:
copy /conf/system-default.conf /conf/startup-config.conf
and:
reboot
Then, similarly, we go to the web interface of the access point (the address is configured automatically via DHCP) and right on the first page, disable the Discovery checkbox in the Nebula Control Center window.
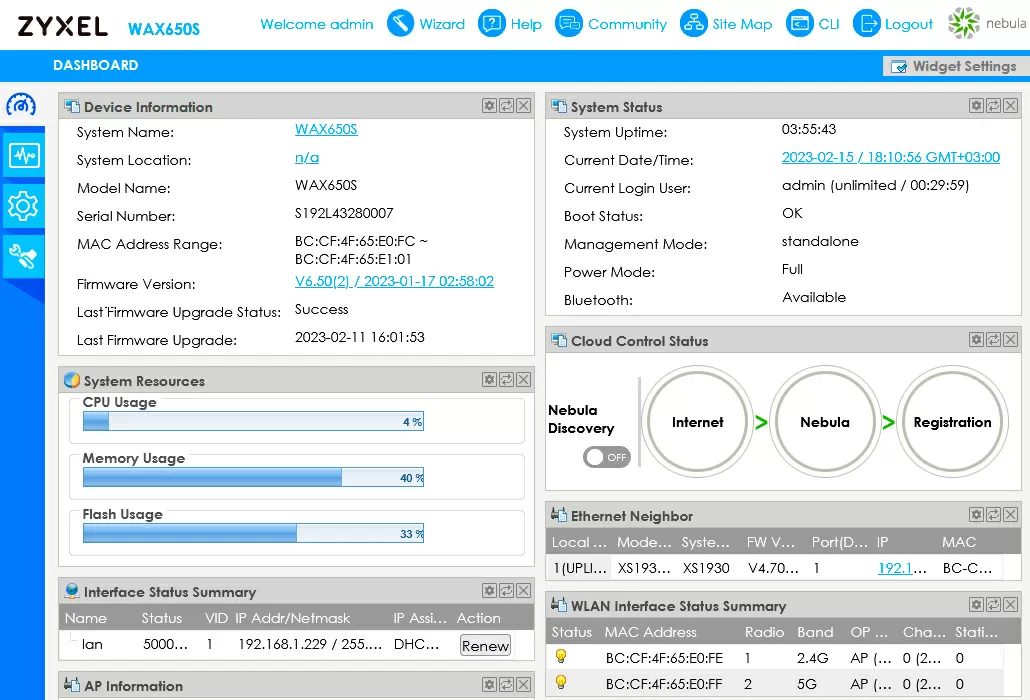
That's it! Now the devices are yours! No one will take anything from you, intercept or block control!
Can I ask a friend from abroad to log into my Nebula account and delete the configuration?
Yes, it is possible, but it makes sense to do it if you have already passed the last step and reset the devices to the default settings.
And what about cloud switches that do not have local management?
Yes, Zyxel has a line of equipment that does not have an autonomous mode of operation at all, but is controlled exclusively through the cloud. For example, these are the switches of the NSW series, which have not yet been widely distributed. For them, it is best to use a VPN or proxy.
That is, you can connect via Proxy?
Fortunately, in the corporate world, clients are often located behind a proxy, so in the settings of each access point, each switch, each gateway, it is possible to register a proxy server for accessing Nebula CC, and perhaps this will turn out to be a saving option, although attempts to bypass locks through a proxy were effectively suppressed back in 2021.
And a proxy can also help in the case when you cannot direct control traffic to Nebula via a VPN, for example, in cases when the device is directly connected to the provider's network without a router. In this case, you need to specify in its settings just the Proxy address in the internal network of your VPN connection, having previously configured Squid on the provider's VPS gateway for this purpose.
Will Nebula work via VPN?
Perhaps this is the most "ecological option". The mechanics here are quite prosaic: a $2 VPS is bought in a "friendly" jurisdiction, where a VPN gateway is configured, and all Nebula traffic is routed through it. There is a slight difficulty here: over switches and access points, you need to have a good router capable of directing certain traffic to a VPN, and today this function is even available in home Keenetics, not to mention business models.
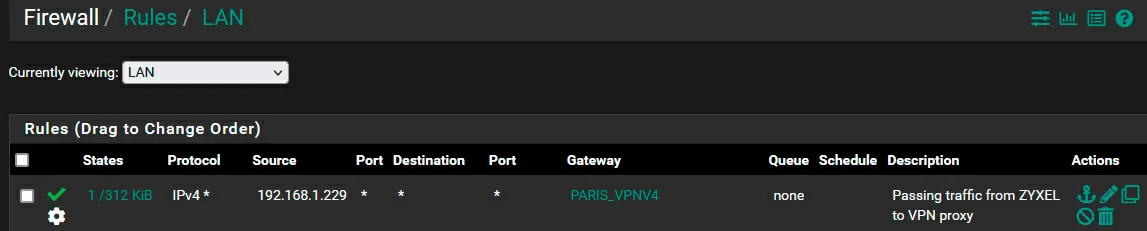
Interestingly, when connecting via VPN (in our case, Paris), the equipment continues to correctly determine the local public IP address, so that some settings tied to the WAN IP connection will not fly off.
In principle, a good good VPN, and even wrapped in Stunnel, can save you for years, maintaining network management in a combat-ready state. But I still do not recommend trying to bypass the blocking via VPN +Stunnel on port 443, which "breaks through" even through the "Great Chinese Firewall" and is not subject to any DPI analysis. No, I don't recommend it, but how can I? What are you? We are law-abiding citizens!
TOTAL: as in the case of access to prohibited sites, a VPN is a salvation, because
! ! ! NEBULA WORKS VIA VPN ! ! !
at the same time, it correctly determines the external IP and prescribes routes to local gateways.
On a positive note
As you can see, the problem is overrated. By itself, the risk of blocking the Nebula service is negligible: today no one blocks unwanted resources by IP addresses, using instead the analysis of DNS queries with the substitution of the response from the server. And even if the iron curtain comes down, cutting you off from the global network, your local network will continue to work: reports will be sent, letters will be accepted, social networks will be opened. In the general chaos, you will have enough time to untie the devices from the cloud and reconfigure them for your tasks, and if you are in the mood, you can start doing it in advance. If you copied the password from the Nebula control panel in advance (I won't remind you anymore!), then most likely you won't even have to climb to the devices with a paper clip by unscrewing the access point from the ceiling.
Do I need to deploy new projects on Nebula now, or should I do it offline?
Nebula greatly simplifies the configuration of Wi-Fi and functions related to security and network monitoring. Considering that in the basic version all this functionality is offered completely free of charge, I see no reason to abandon these features. I believe that if the Iron Curtain does come down, disabling the cloud will be the least of the problems that have fallen on the IT organization. If you serve networks on an outsource basis, these risks can be shifted to the client or attributed to force majeure.
However, it should be borne in mind that Nebula Control Center is not a panacea, and as soon as you need a deep network setup (L3 on switches, L7 on gateways), you will have to take the devices offline and configure them the old-fashioned way, via WebUI or CLI (read about what NGFW from Zyxel can do in our review). Therefore, I would advise you to proceed in this matter from the needs of your client, your organization and your network, and not to cause panic like "oh, Nebula will be turned off."
Michael Degtjarev (aka LIKE OFF)
16/02.2023