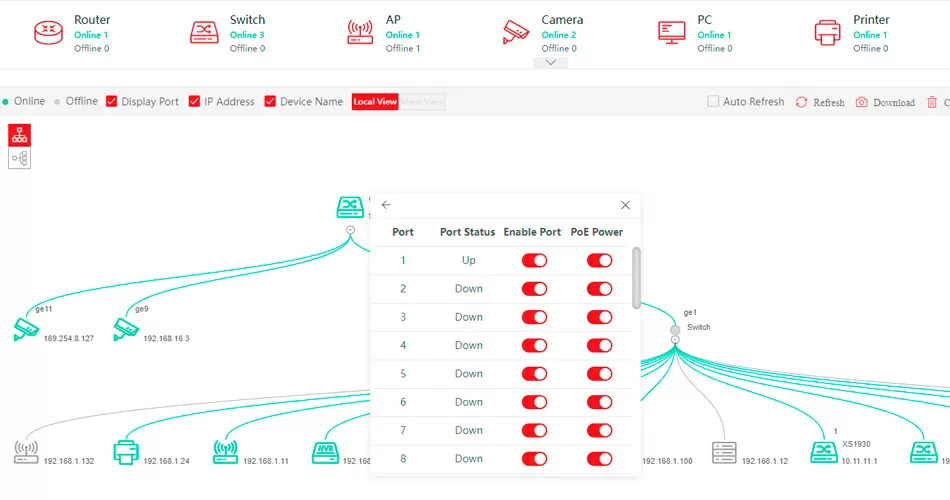
Following the recommendations of "best practice", network devices of various purposes, such as IoT, work computers, smartphones, guest devices, should always be located in different subnets, and ideally terminated through a common security gateway, however, in some cases, for example, when the gateway does not cope with the flow of traffic, distribution by subnets it can be assigned to a network switch to separate different devices by VLANs, thus separating access to different networks already at a reliable and fast L2 level. Here the question arises, how to cope with a large fleet of devices, so as not to prescribe rules for each individually, and to abandon insecure authorization by MAC address?