Protecting the company's network with Zyxel USG Flex 100AX
Zyxel USG Flex 100AX is an entry–level security gateway that is designed for installation in small offices and branches, in cases where the company has strict security requirements or has a complex multi-rank network in which it would be nice to limit employee access to various social networks and unnecessary resources and have an additional line of protection of the network perimeter.
Security gateway with Wi-Fi 6 on board
This gateway is interesting because it has a built-in 802.11ax Wi-Fi module (Wi-Fi6) with a 2x2 antenna formula and a total speed of 1800 Mbit/s (600 Mbit/s for 2.4 GHz and 1200 Mbit/s for 5 GHz with a maximum channel width of 80 MHz), which allows you to save at least on one access point where it will be installed, and given that the USG Flex 100AX does not have fans, you can hang it in a closet under the ceiling in the same room where people are.
For larger wireless networks, it is possible to switch the Zyxel USG Flex 100AX to Wi-Fi controller mode to control Zyxel access points, and at the time of preparing the review, 23 models of modern AP from this manufacturer of the NWA, WAC and WAX series were supported. By default, management of up to 8 access points with an extension of up to 24 is supported when purchasing a license. However, it should be borne in mind that switching to Wi-Fi controller mode immediately disables the built-in wireless module in the gateway, and you lose one of the main advantages of this model. So I recommend using the Zyxel Nebula cloud controller for wireless networks (by the way, you can read here about whether Nebula will work in case of disconnection from the global Internet).
Zyxel has a very interesting Secure Wi-Fi feature for connecting wireless clients via VPN directly to the central gateway of the enterprise (we talked about it in our review). It is also implemented here, but according to the license subscription system.
From the point of view of Wi-Fi, the USG Flex 100AX model is somewhere at the level of average home routers, but it has a reserve for the future: if the wireless infrastructure at the facility begins to grow, this gateway is ready for this, although you will have to pay for licenses.
Design features of the Zyxel USG Flex 100AX
The security gateway is assembled in a compact aluminum housing designed for desktop installation. There are indicators on the front side, on the back side there is 1 WAN port, 4 LAN ports (of which one can be configured as WAN2/OPT), a console port and antenna sockets. Rack mounting is not provided, so if you put the device in a closet, then only on a shelf, with antennas to the wall.
The device has completely passive cooling with all the advantages that follow from this – noiselessness, reliability and the ability to work in a dusty room. There is not a single electrolytic capacitor in the design of the Zyxel USG Flex100AX, so there is not much to age in this model, the stated operating time is 766,228.2 hours, that is, 87 years. The main processor and memory chips are covered with a metal shield to protect against EMR. The wireless module is also shielded and covered by a massive flat radiator.
Lightning protection is not provided on the ports, so the Zyxel USG Flex 100AX is plugged into an outlet without grounding and does not require a separate "ground" output to the housing.
Features of VPN support
The Zyxel USG Flex 100AX supports IKEv2, IPsec, SSL and L2TP/IPsec protocols. As before, there is neither OpenVPN nor Wireguard, but to implement a hybrid infrastructure with cloud services, Microsoft Azure and Amazon VPC VPN support is implemented.
The IPsec VPN service is quite well developed – several connection usage scenarios are supported (network-to-network, server, client, virtual VTI interface), certificate verification during authentication, work in the zvezda topology when the gateway acts as a hub.
Security functionality for Zero-Trust networks
Today, zero–trust networks are the main trend in the world of corporate information security. If you are not familiar with Zero Trust Protection (ZTP), then in a nutshell these are networks in which there are no shared corporate resources, and access to each node, each service and each resource is prescribed individually for each user. Most services are hosted on port 443 and work via the Web, and each user or each node has strictly defined rules for what they can do on the Internet, and everything else is not allowed. The implementation of ZTP requires the use of powerful NGFW (Next Generation Firewall) class security gateways that combine a traditional Firewall, an Internet proxy service with an antivirus, and long, long access policies with updatable signatures. Practically, all this is available in Zyxel USG 100 AX, so if you are faced with the task of building a new ZTP-level network, you may be able to do it on Zyxel.
Web surfing Security
The logic of restrictions in Zyxel USG Flex 100AX is as follows: the rules by which certain resources are limited are collected in protection profiles, such as, for example, "banning visits to nonsense during working hours", "filtering unnecessary sites for children" and so on. Well, you just apply the profile itself to the direction of traffic between zones, such as LAN-WAN.
Well, you just apply the profile itself to the direction of traffic between zones, such as LAN-WAN.
Application Patrol and BandWidth Monitoring
If your company implements the principle of using personal gadgets on a shared network, then of course smartphones and laptops are ways to generate spurious traffic without user participation: these are constant updates, background surveillance and telemetry, messengers, etc. Modern devices have learned to understand this pile of requests by implementing the IDS principle: if a packet is sent from a device to such and such an address with such and such a port, then most likely it is Skype, and if the packet came from such and such an address to such and such a port, then it is Angry Birds.
A distinctive feature of Application Patrol is that it does not "listen" to packets, and encryption from applications is not an obstacle for it. The ability to distinguish an application by the characters of not only outgoing but also incoming packets depends on the quality of the signatures used. Please note that you are not blocking the exit through the browser, but the operation of the applications themselves on smartphones.
But in general, sometimes it is more important to prioritize different types of traffic, which is configured via the BWM tab. You can use DSCP codes to change routing altogether, directing one traffic through a VPN, another through a terrestrial channel, and the third to drop without regret, but there is no possibility to install different DSCP code for different applications.
IDP - intrusion prevention and E-Mail protection
Intrusion Detection Prevention works as an independent filter, whose task is to prevent data leakage beyond the perimeter in the event of malicious code running inside the network or protecting devices from external attacks. In fact, the filtering functions are performed by many Suricata and Athena packages, and the filter itself can be limited for some services (mail, DNS, Web), or you can keep it enabled for all. By the way, here you can add filtering rules yourself by setting very detailed connection parameters, including speed, operating system, identifier, fragmentation and packet contents. Custom signatures can be downloaded from a USB flash drive.
The mail protection service can work for SMTP and POP3 protocols, but in the Zyxel Flex series, its protection is limited to antivirus scanning and a DNSBL-based spam filter. To protect against spoofing, it is possible to drop mail connections when a certain limit is reached, and when you activate the Gold license, you will also receive anti-phishing protection.
Reputation and context filters
The reputation filter is an independent engine that restricts access to malicious sites through DNS substitution of responses to SNI (server name indicator) queries. Since SNI requests are transmitted at the very beginning of connection establishment, even before encryption is installed, they can easily be intercepted by the gateway proxy server without using a MITM attack with decryption of traffic, that is, completely transparent to clients. The reputation filter does not need to be applied to traffic directions, but it just turns on immediately for WAN.
Antivirus filter
As I said, the Zyxel USG Flex 100AX security gateway uses two types of antivirus filters: cloud and built-in. As a rule, such protection is implemented through a built-in proxy: when downloading a file, it is first saved to the device's memory, quickly checked by one of the selected methods, and then transmitted to the user. For the client, this process looks completely transparent, everything works the same as with an ordinary Internet connection, with the only difference that you will not download the infected file to your computer.
Blocking infected files is not configurable: just the URL where the malware is located, bypassing the filter will work, and when connected via Zyxel USG Flex, it will give the 404th error. In order to detect Malware in an encrypted connection, you need to enable content filtering.
Content filtering
This is a real censorship, due to which you can restrict access only to the correct sites or, conversely, ban individual sites and entire categories. Directory lists are updated in the same way as antivirus signatures, and if the site is suddenly not in the database, you can either disable it or issue it after a warning like "we cannot be sure of your safety... Blah, blah, blah."
Content filtering works not only by URLs, but also by keywords, it can be applied to one or more "LAN-WAN" directions, and to implement it on your network devices, you need to install a Zyxel trust certificate and enable an encrypted traffic sniffer, that is, to carry out a MITM attack. I want to note that SSL inspection is needed only to check the entire URL, that is, to block by keywords, and domain blocking works the same way as URL Reputation - by SNI.
That is, let's do it again and in more detail.
- Step 1 - You create a certificate in Zyxel USG Flex 100 AX,
- Step 2 - You create an SSL inspector profile with httpS traffic encryption/decryption
- Step 3 - You create a profile with content filtering
- Step 4 - You apply a profile with content filtering to the "LAN-WAN" traffic direction
- Step 5 - You install certificates on client machines
After that, you will have a substitution of certificates for those that are installed by the security gateway. Now you can block potentially unwanted sites and track the statistics that your employees or guests use to go where they don't need to. However, this trick works just as well with Google Chrome as it does not work with Mozilla Firefox - if you use this browser, you will have to add the certificate directly to Firefox. The browser skips and opens some sites, and swears at some of them for trying to eavesdrop on the connection.
Licenses
Many useful NGFW functions in the Zyxel USG Flex 100AX are provided by subscription, and only a trial for 30 days is available in the basic device, here is a list of them:
- Sandbox
- Reputation Filter
- Intrusion Prevention (IDP/IPS)
- Application Patrol
- Anti-spam
- Content filtering
- SecuReporter Analytics
- Joint detection and response
This is not surprising, since network protection is based on signature lists and cloud file analysis, and all modern IT security is sold by paid subscription.
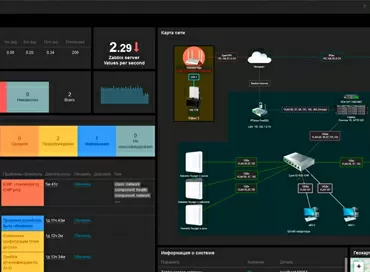
Cloud management via Nebula Control Center
The gateways of the USG Flex series have received a new type of connection to the Zyxel Nebula cloud service – monitoring mode. It is designed for those cases when the customer wants to connect their entire network infrastructure to Nebula, but does not want to lose direct access and control over security settings directly at the gateway.
And to be honest, for several years of Nebula's existence, the manufacturer has not been able to add all the rich functionality that is available in L3 switches and network gateways, so using the CLI or WebUI to configure directly on the device has not gone anywhere. Now this problem has been solved, and you can, for example, control the wireless network via Nebula (the access point control mechanism is excellent there) and control the rest of the network stack directly, including monitoring using Zabbix, Netdata, LOKI, Grafana, etc.
Recommendations when ordering
By itself, the Zyxel USG Flex 100 series fits perfectly into the concept of peripheral (Edge) computing, and into the model of an extensive network with branches, and even into the ideology of abandoning network centralization and cloud services in favor of building complex secure networks in which all resources used are local, where separate subnets are allocated for employees, for IoT and for administrative staff. For myself, I have not found an answer to the question of whether Wi-Fi is needed in such a gateway, and what a wireless network would look like, on top of which the USG Flex 100AX would be installed, since the fact that when the wireless access point controller is turned on, the built-in radio module is turned off, calls into question the expediency of its installation. What did the manufacturer think that Wi-Fi would only be in one place near the gateway, or that you would have two Wi-Fi networks – one on the access points, the other on the gateway? No, I don't understand that.
In terms of security, yes, the Zyxel USG Flex 100 is one of the cheapest NGFWs on the market, with full support for cloud analysis, SSL bumpinging, reputation filters and signature support. To start building zero–trust networks, this is an excellent hardware solution that will work even if the iron curtain is lowered.
Michael Degtjarev (aka LIKE OFF)
03/02.2024