Zyxel WAX650S review and test: flagship access point with Secure Wi-Fi technology
Today we are considering the top Wi-Fi 6 access point made by Zyxel. This is a truly "omnivorous" access point, designed for installation both in rooms with a large number of people, and in technological buildings of production, ensuring the operation of IoT. This model uses a "Smart antenna" with a dedicated module for scanning the range, capable of forming a directional beam, individual for each subscriber, which allows, firstly,to increase the range of the connection compared to conventional AP, and secondly, to confidently work out the client's movements in space, including in the presence of interference from other base stations. Previously, we saw something similar with expensive AP from Huawei, and it is very nice that Zyxel also has such a solution.
But not only the WAX650S model is interesting for the hardware part - Zyxel promotes Secure Wi-Fi technology, this is when the AP itself connects to the corporate gateway via a VPN channel and provides access to the client to the office network using external authorization, for example via Google. As a result, the client gets access to all the network resources of the organization from any device, and can access the Internet using security policies set by the organization's administrator. This is just a godsend for remote work and various field events, but about everything in order.
Interior
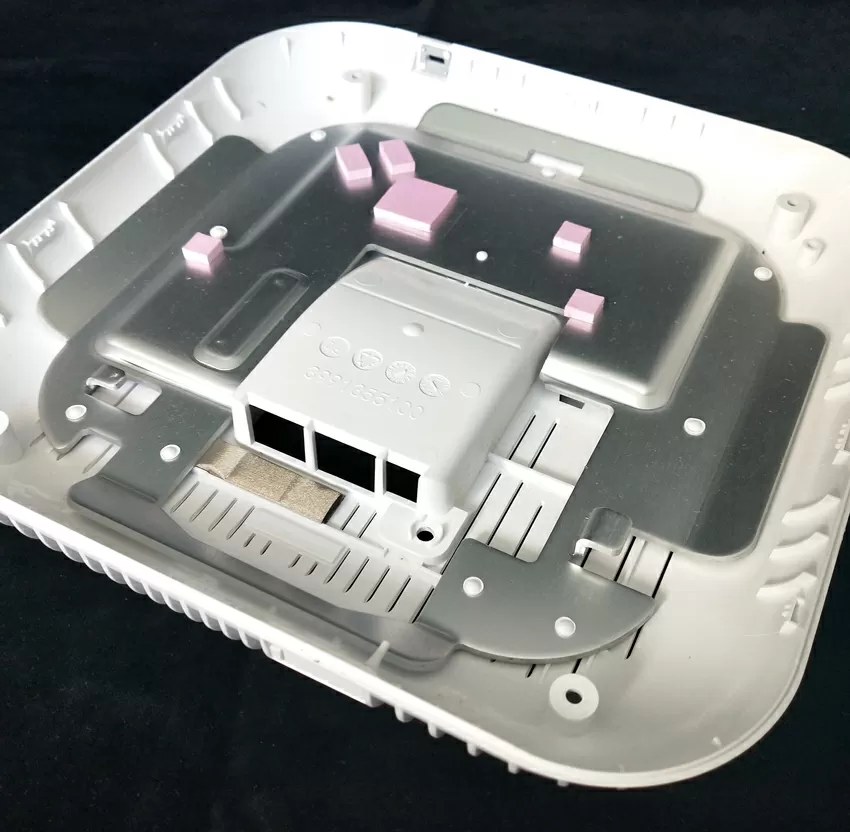
The Zyxel WAX650S access point looks no different from its simpler counterparts: even the edges of the case, resembling a radiator, are made of plastic, more for show. And the only thing that gives out a high class of the device is a network port of the 5GBase-T standard with PoE support, as well as a second ordinary 1-Gigabit port for LAN. The maximum declared power consumption of the device is 31 watts (a switch with 802.3 BT support is required), but judging by the cooling system, it is unlikely that the TD will consume more than 20 watts.
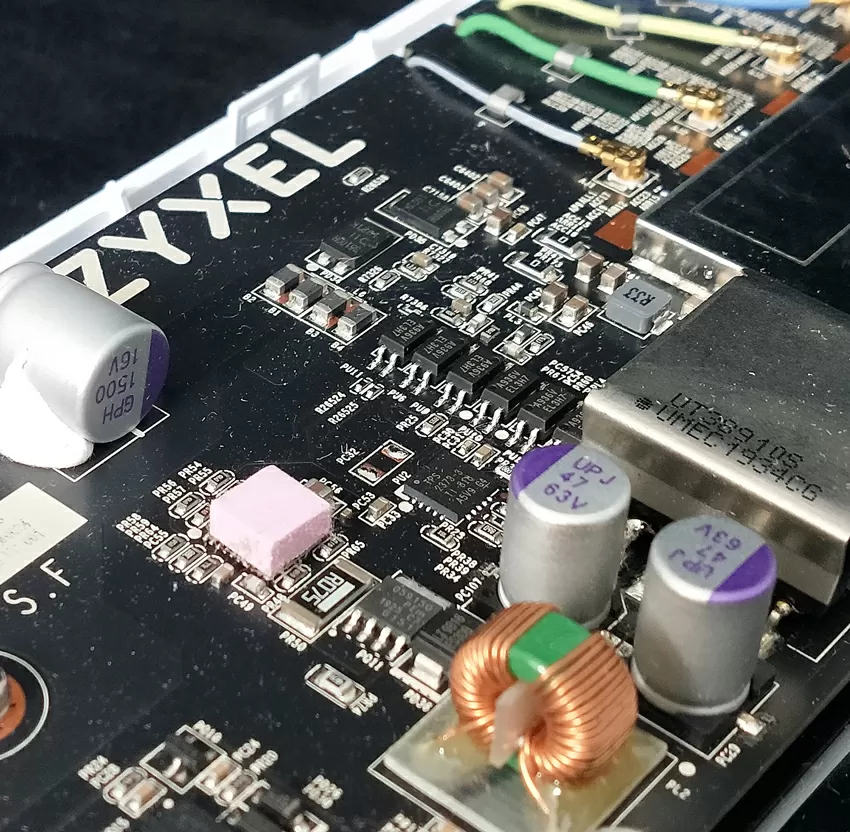
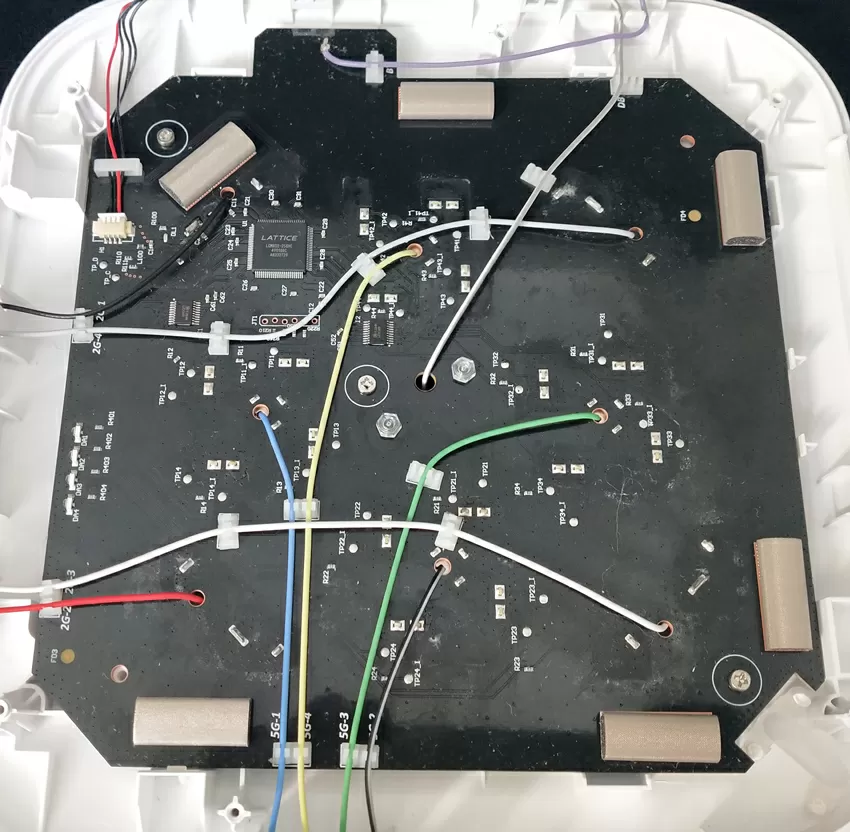
Zyxel WAX650S has a complex design: all the main elements (radio modules and processor) are placed on the front side in an individual radio-insulated case. When assembled, a thick aluminum plate is installed on top of the motherboard, which serves for heat removal from the hottest elements and additional shielding.
On the reverse side, the motherboard is closed by a large steel casing that serves to shield from the antenna module and heat sink from the reverse side of the chips on the motherboard. As you can see, Zyxel takes the most responsible approach to the issue of shielding, and not only in order to protect the TD electronics from background radio noise, but also in order to reduce its own radiation from the back of the case and not interfere with other equipment behind the wall or on another floor. The manufacturer also emphasizes that the WAX650S model uses 4G/5G band filtering from cell towers and repeaters, so that the device can work even if cellular antennas are installed next to it.
In the flagship models of Wi-Fi access points, an additional radio module is often installed, which continuously scans both the 2.4 and 5 GHz frequency bands and adjusts the main modules taking into account the interference that occurs in real time. Sometimes developers leave it possible to switch it to the normal radio mode, adding a couple more spatial streams to the existing ones, but the Zyxel WAX650S has an additional module that only serves to adjust to the radio environment using heuristic analysis and machine learning.
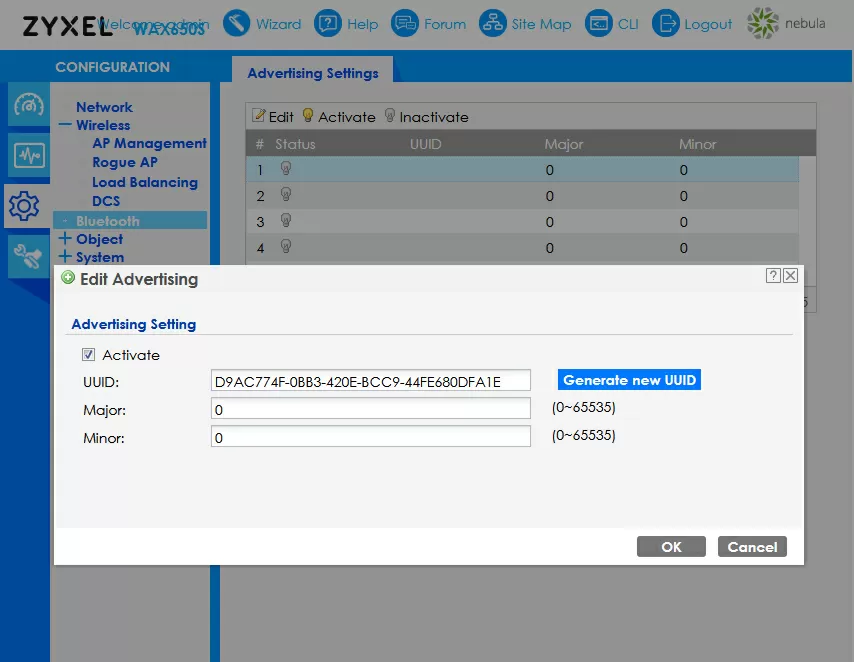
For integration into the IoT world, there is support for BLE Beacon in the form of a built-in module. Let me remind you that Bluetooth Low Energy (BLE) allows you to display a message on its screen or launch an application when a client approaches with a smartphone with Bluetooth enabled. This feature can be used, for example, for navigation in shopping centers, personnel control systems, installation of face recognition terminals, etc.
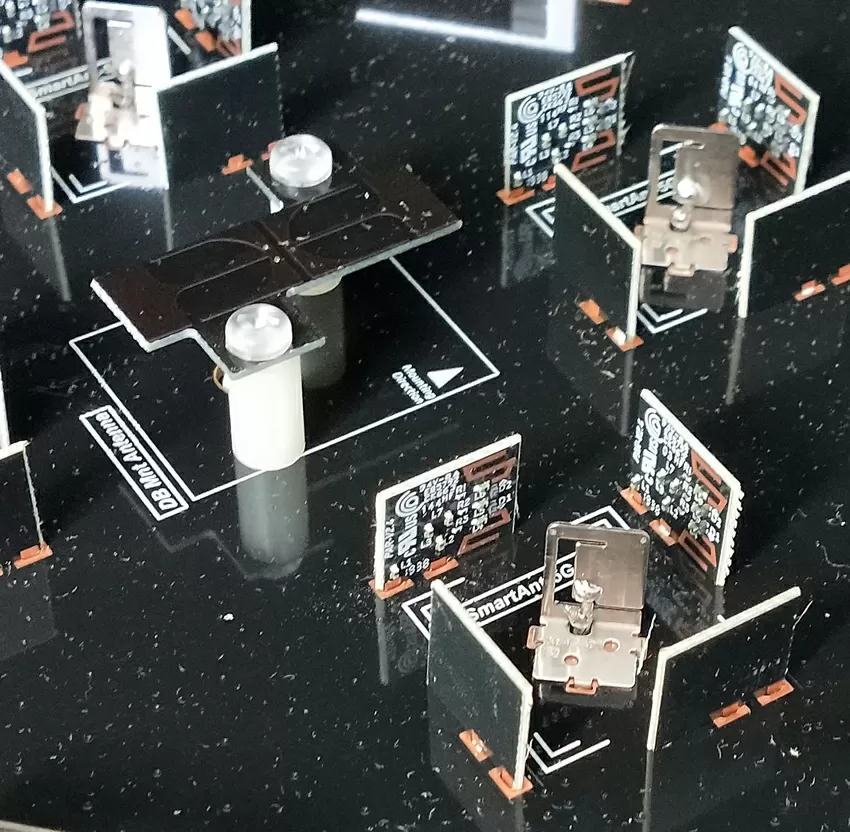
OK, having dealt with the design of the motherboard, we go directly to the antenna. Any "smart antenna" has more elements in the design than a simple one, since it consists of many radiating parts controlled by the device's software. In the case of access points, the main task of smart antennas is to direct the radiation power in the direction where the client device is located, and not to clog the air in other directions. Technologically, smart antennas are small narrowly directed planar antennas assembled in arrays and controlled by a separate controller. Usually, it is enough to have emitters directed in 4 directions to cover the entire space around the access point as much as possible. In our case, for the 5 GHz band, 4 clusters of 5 emitters each are used in the antenna. For vertical polarization antennas, 4 small boards are installed, which are controlled by a controller located on the back side of the antenna.
For horizontal polarization, simple metal emitters are quite consciously used, with their help a frontal or omnidirectional beam is formed, so it is quite logical that Zyxel did not use prefabricated structures for them.
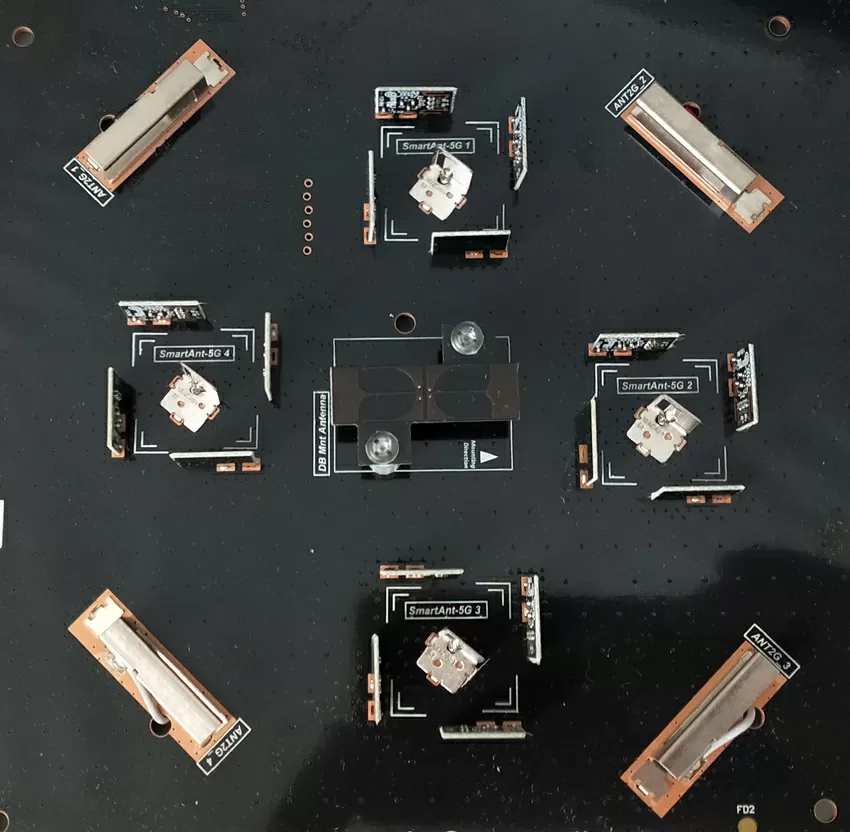
In the middle of the board there is an antenna of an additional module for adjusting to the radio frequency situation. As a rule, thanks to it, modern access points no longer conflict with microwaves, wireless keyboards/joysticks and remote controls.
For the 2.4 GHz band, conventional L-shaped metal emitters with horizontal polarization are used. The "smart antenna" technology is not used for this range, although probably in vain-robots and various IoT equipment often use the non-alternative 2.4 GHz band.
And now let's compare the characteristics of the antennas according to the stated numbers: for the 2.4 GHz band, Zyxel claims a gain of only 3 dB, which is a very average indicator, but for 5 GHz - as much as 5.8 dB, a record value for access points with built-in antennas.
Software
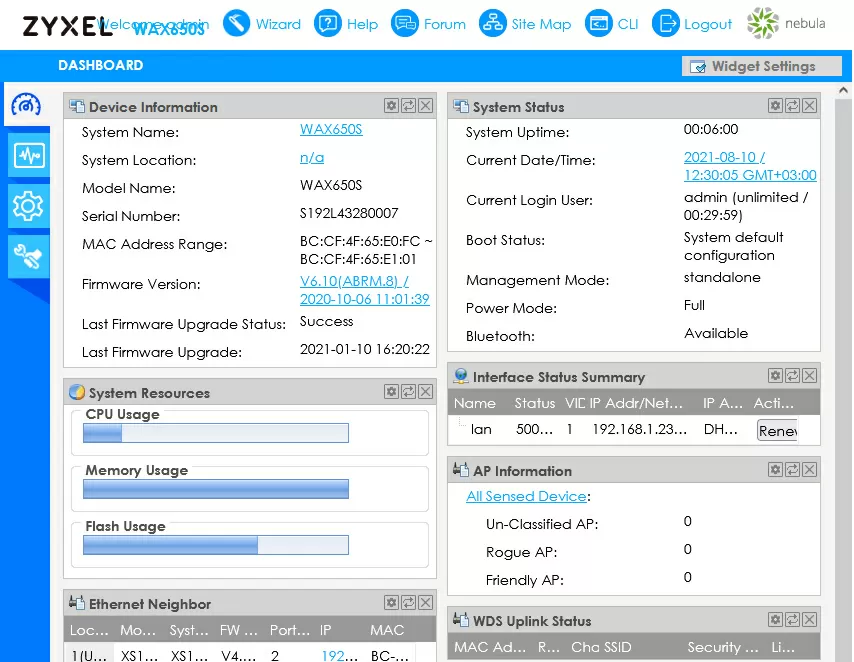
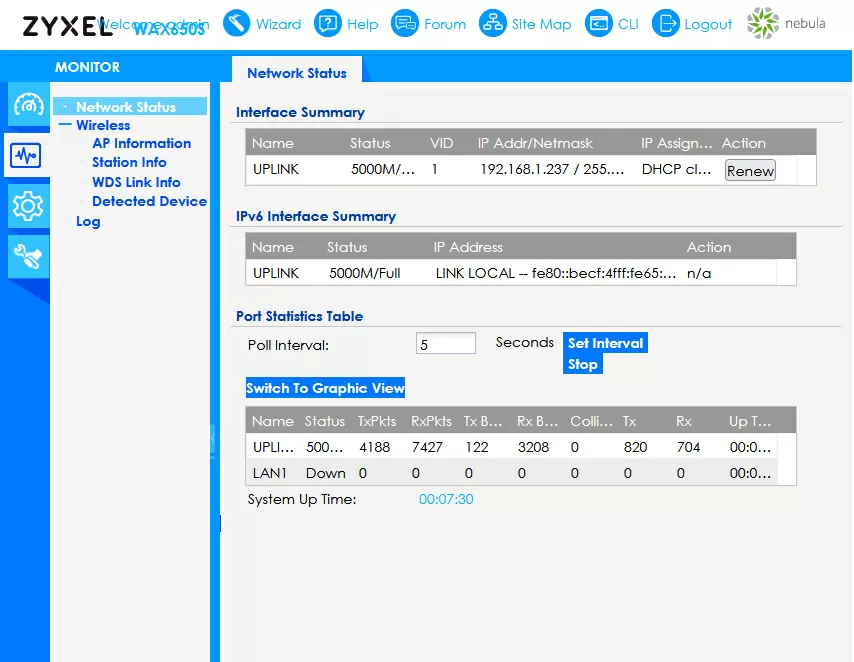
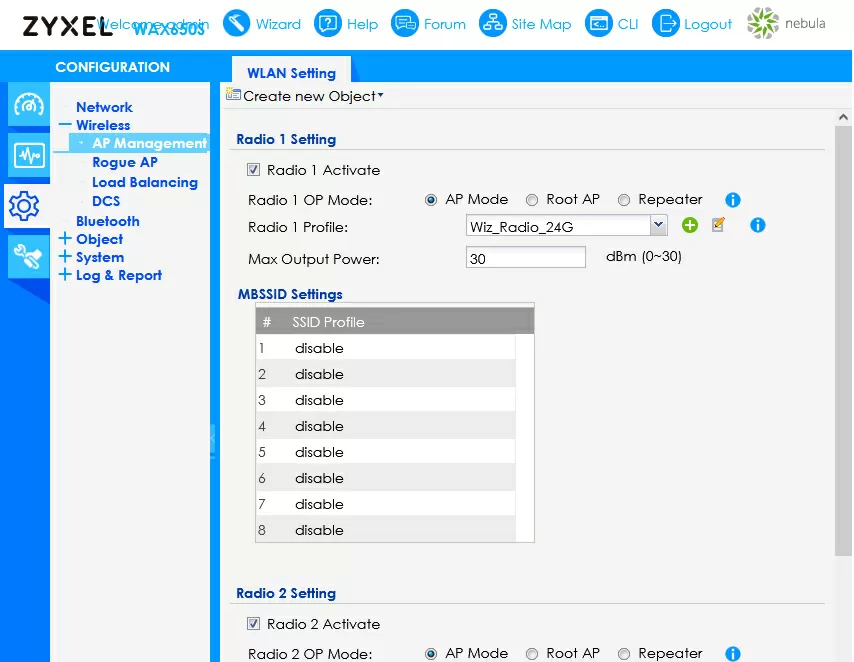
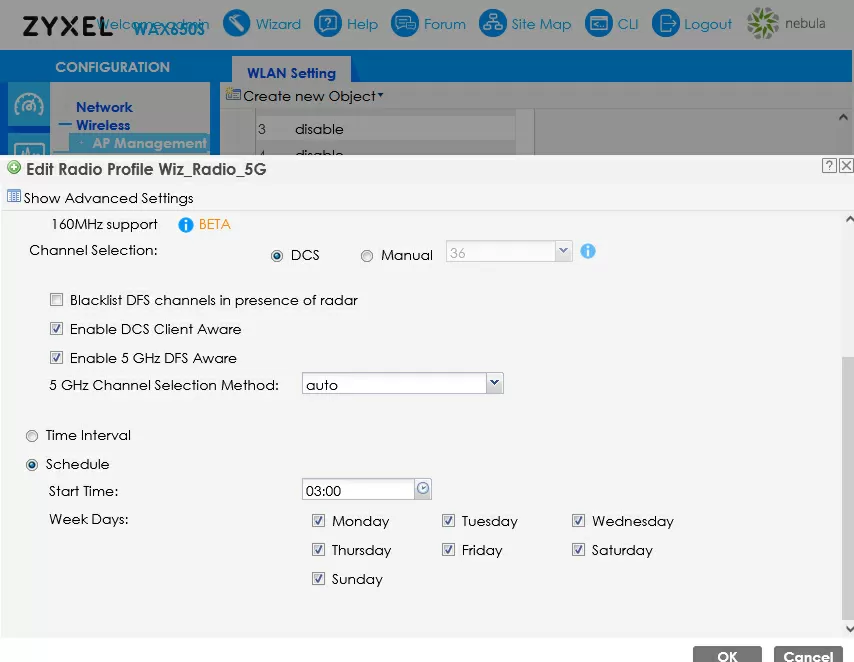
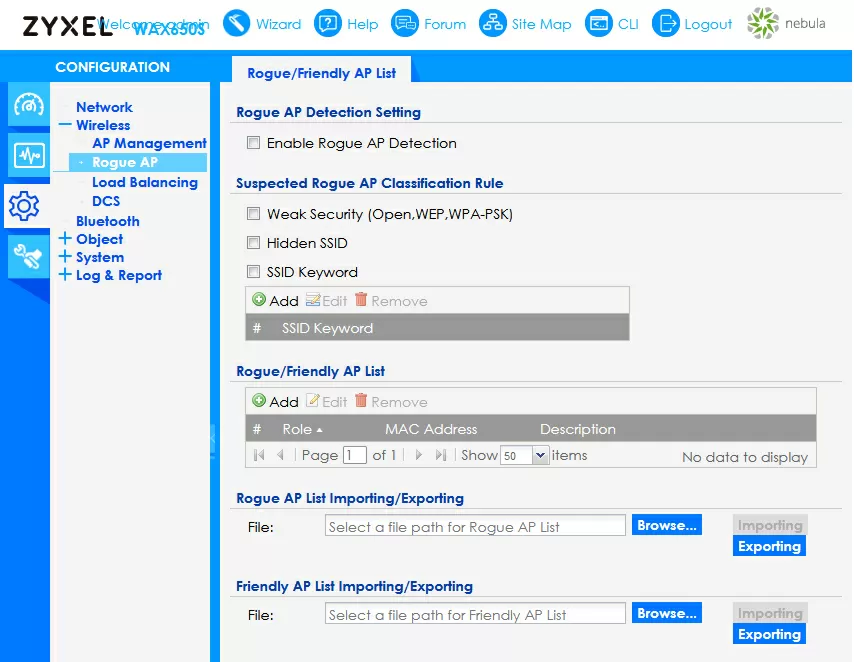
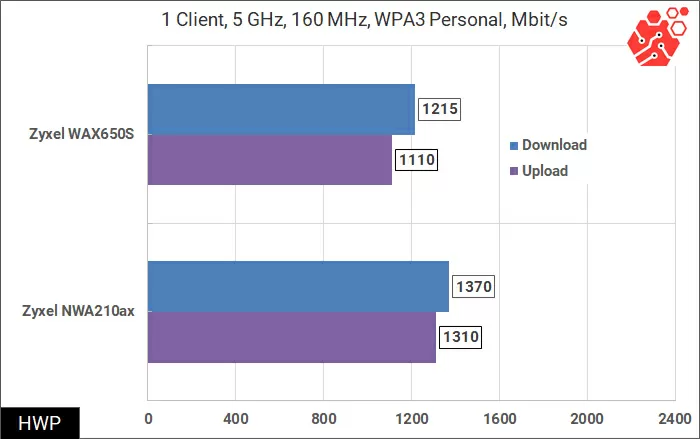
The built-in access point management interface has not changed for Zyxel for years, and WAX650S is no exception. The configuration of wireless networks is implemented through profiles, which for some reason cannot be renamed. For each of the frequency bands, you can enable up to 8 wireless networks, each with its own SSID and its own security settings. For full support of Wi-Fi 6, there is an implementation of WPA3, and for the 5 GHz band, a channel with a width of 160 MHz is supported, although so far in the form of a beta version.
Among the settings, there is also a very interesting option to enable maximum power consumption, and this is the first time I have encountered this: I have met the minimum power in the settings, but not the maximum. This is an option for those cases when passive PoE injectors are used and the standard is not agreed, 802.11bt or the point is connected to 802.11at - in these cases, the point operates in a limited mode (2 antennas are disabled). By enabling this option, the restrictions are removed and the point works as usual.
Secure Wi-Fi
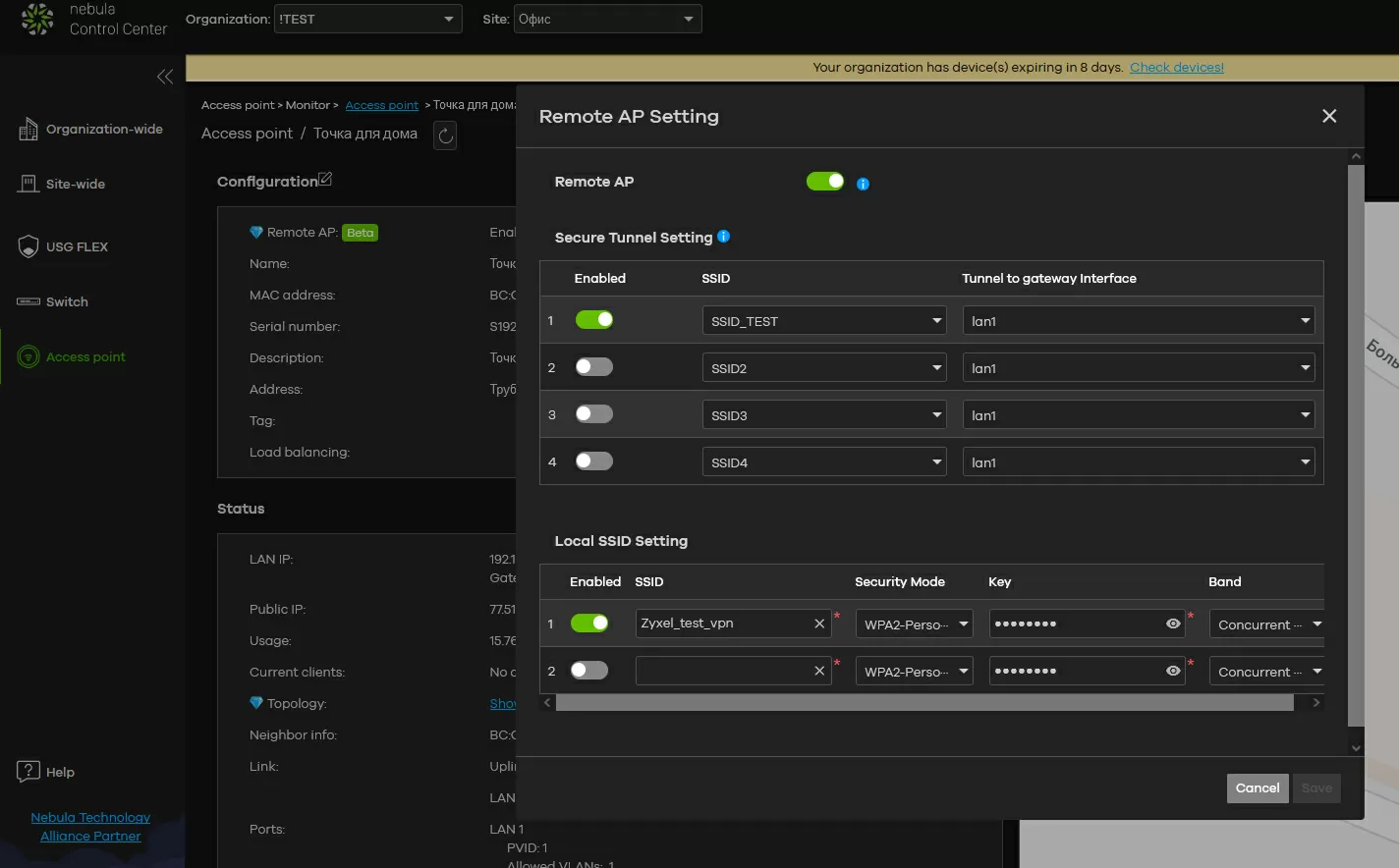
Secure Wi-Fi technology allows you to create a VPN tunnel between the access point and the access gateways of the USG Flex series (see the Zyxel USG Flex 500 review), ATP (see the Zyxel ATP500 review) and VPN so that the presence of a VPN tunnel is transparent for the client and does not require any additional settings. This is necessary so that the client, connecting to some SSID, as to a regular Wi-Fi network, immediately gets access to all office resources: network folders and printers, any applications, without thinking about whether they use encryption to exchange data with the client device or not.
From the point of view of the head office, using a consolidated VPN channel "Gateway-access point" is cheaper than "gateway-client", because here you can save on the number of VPN channels that can be shared through the access point to many users. It also makes it possible to centralize access to the Internet for employees, applying corporate security policies and restrictions prescribed on the access gateway to them, and wrapping all employees ' Internet traffic through it.
Naturally, since this is a proprietary Zyxel technology, it works between access points with Secure Wi-Fi support and gateways of the USG Flex, ATP and VPN series. The configuration is conveniently performed through the Nebula Flex management system (although it is also available offline), and the administrator does not need to specify either passwords or VPN channel parameters. IPsec is used for encryption, which is supported by devices at the hardware level, and when accessing via Secure Wi-Fi, the delays associated with wrapping traffic in a VPN are not felt.
From a practical point of view, this technology is also convenient because using an access point as a wireless repeater of your VPN, you can configure authorization by MAC address, via RADIUS or WPA3 to increase security, and again-to reduce and facilitate the configuration of policies on client devices.
Google Authentication
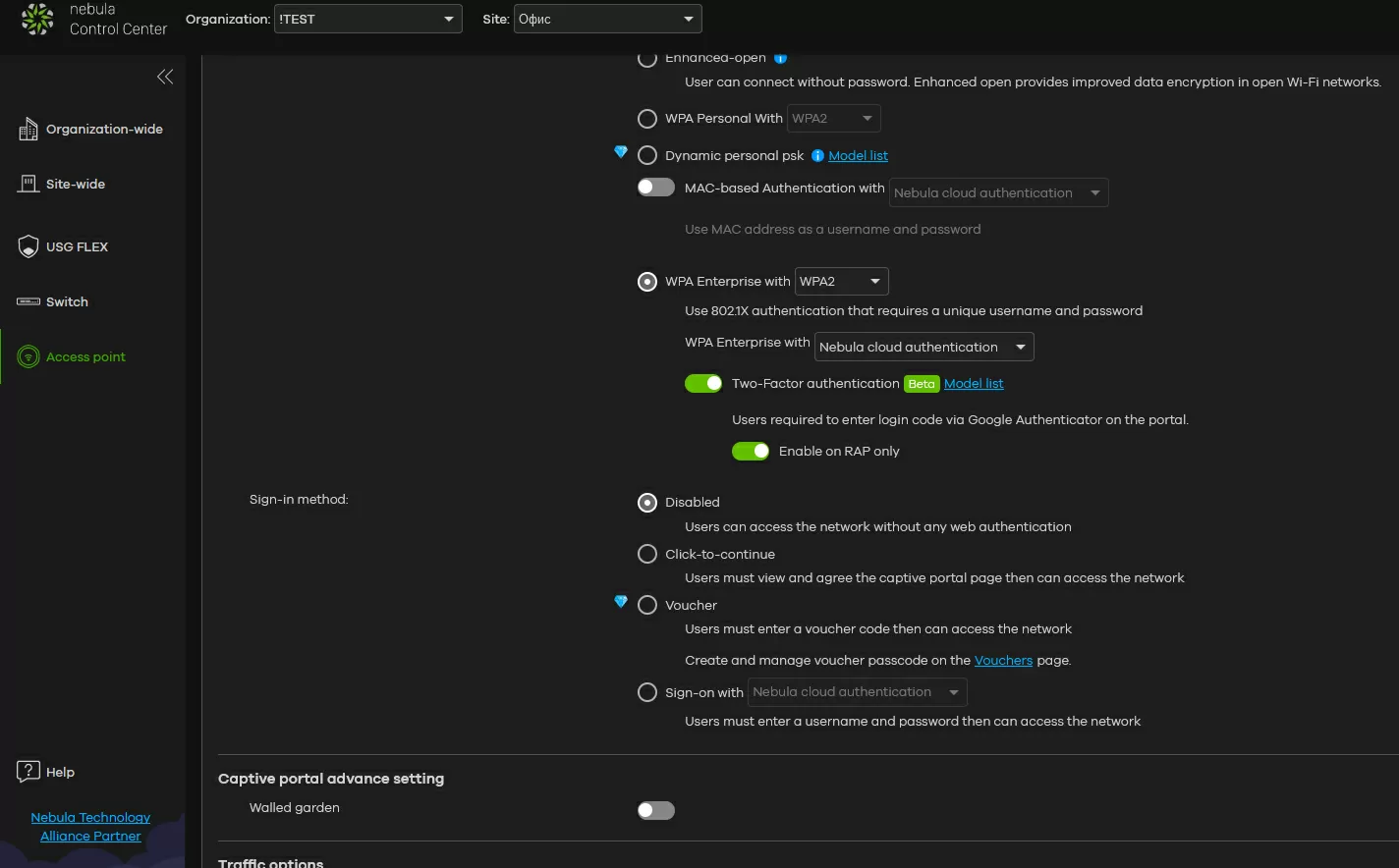
One of the additional means of improving security today is increasingly authentication through third-party services. Previously, we all encountered a confirmation code coming via SMS, and today it is replaced by Google authentication, which does not require payment for SMS notifications. The developers recently added the integration of this feature to the USG Flex security gateways and to the access points themselves, so in our case, Google Auth can be used without a gateway.
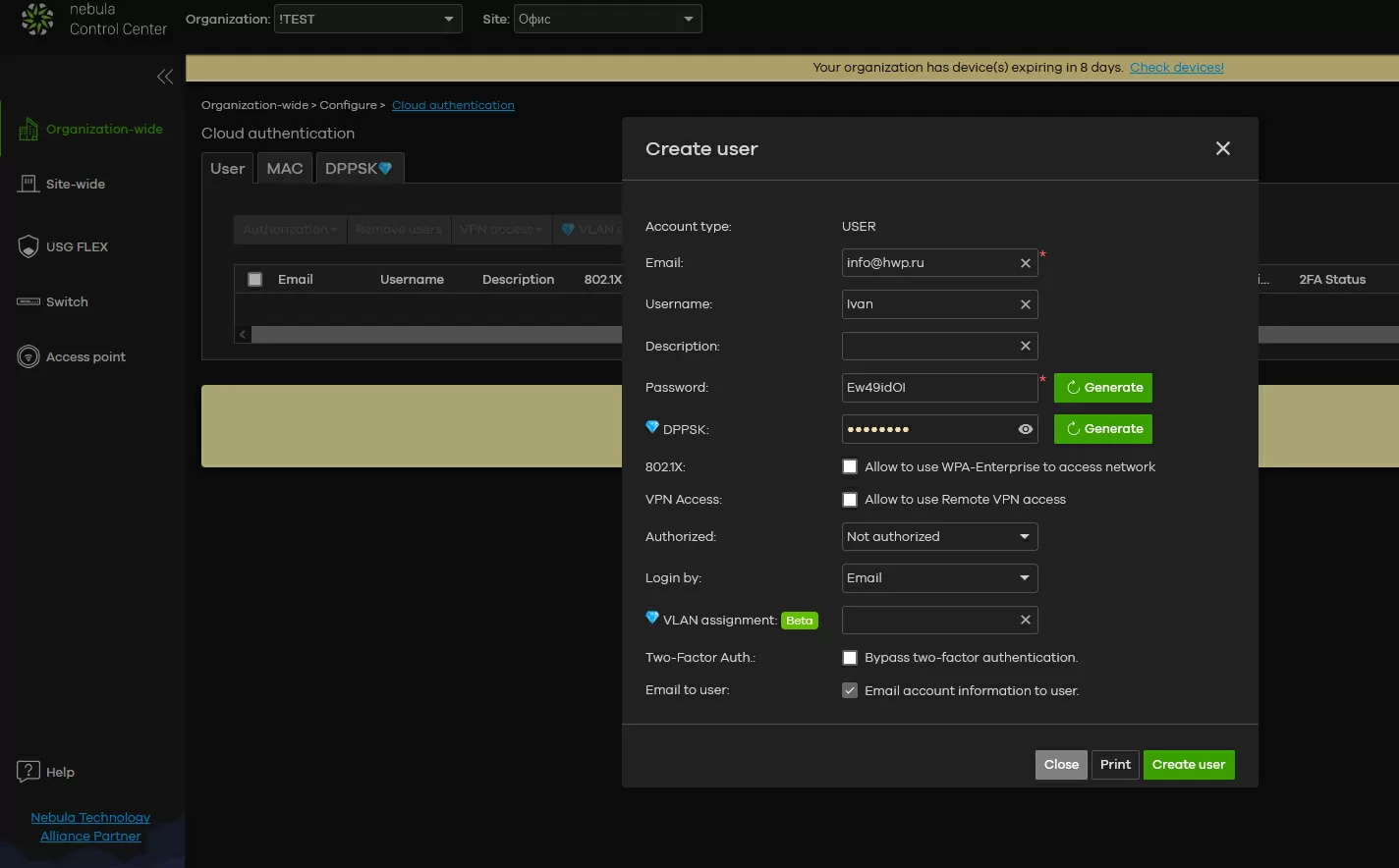
On the part of the network administrator, the configuration consists in creating an account for each user on the gateway containing his login and password. You will have to fill in the list of users manually through the Nebula Control Center. After creating a user, an email arrives to his mailbox with a link to download the Google Authenticator application and a QR code for adding a Wi-Fi access service in this application.
From the user's side, the process looks like this: to connect to a wireless network, not just a password is used, but a pair-a login in the form of an E-Mail and a password unique for each user. When connecting to the network, you need to open a browser and try to go to any address - the user will be automatically prompted to enter the access code from the Google Authenticator program, after which the user will get access to the network with all available rights.
On a smartphone, authentication via Google is not very convenient: due to switching between the Google Authenticator application and the browser, you forget what numbers you had to enter there, and if you use a third-party browser, for example Firefox or Brave, it is still complicated by the fact that the default browser is launched for identification on the network.
But no matter how complicated this method may seem, instead of the usual Wi-Fi password, you get a list of users and three lines for identification: an email box, a password and a dynamic code of a third-party service. It will be extremely difficult to compromise such a sequence.
Test bench
During testing, we will check the theoretically maximum performance of the access point at a distance of 2 meters. To do this, we will equip the test stand with a Wi-Fi adapter based on Intel AX200, connect the access point to a 2.5-Gigabit network port (the Intel X550-T2 card works in this mode) and we will check the speed, use iPerf 3.
 |
Test bench configuration:
NIC:
OS:
|
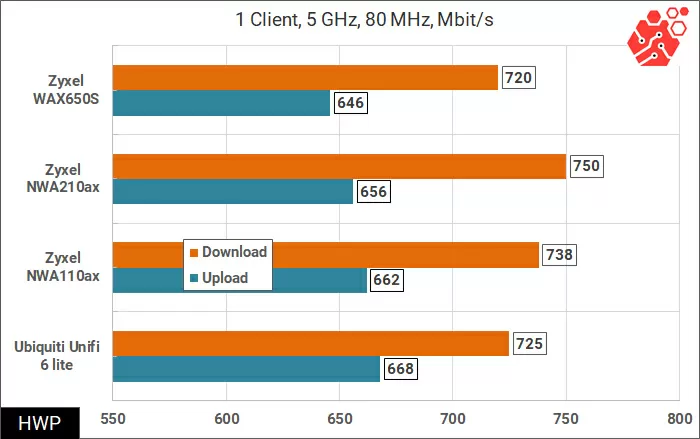
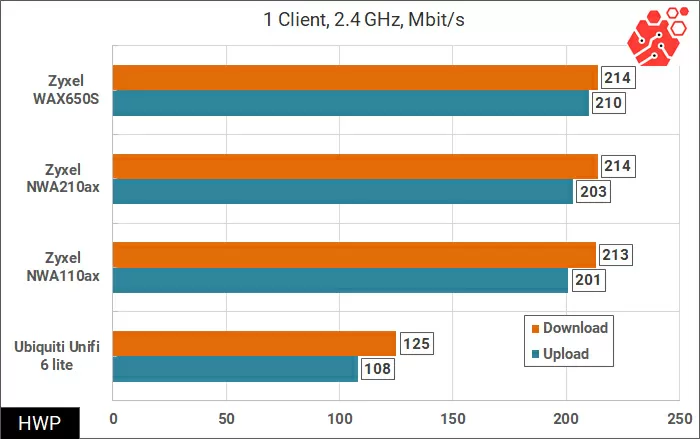
In this test, we will use 1 client connection with a channel width of 80 and 160 MHz. I want to note that since the Intel AX200 network cards are quite raw, only one of the two cards was used in our test after the next driver update,
the speed of which also differed from the results of previous measurements. Due to the error, the top-end WAX650S works the same as a simpler analog, but this is not fundamentally important. In this case, the error greatly affects the measurements.
Conclusions
It is very nice that access points are developing not only in the direction of speed, but also in the direction of functionality, and finally we see what synergy a single-brand kit gives with a common management system, thanks to which support for Google 2-factor authentication has appeared. In general, delegating some security issues to third-party vendors (Zyxel, Google) is an established trend that will eventually only displace traditional approaches to security configuration. Well, judge for yourself, creating a VPN tunnel between the gateway and the access point is two mouse clicks, and there is no need to invade the user's device: regardless of the operating system, both smartphones and robots and smart things will direct traffic through the central gateway, which means that their administration will become cheaper and more efficient, and above all, this will be noticeable in peripheral (Edge) installations.
Two-factor authentication makes it pointless to attack the Wi-Fi password, since each user now has their own access keys to the corporate network. This method of protection is simple and free, and the ability to close access to the Google Authenticator application via biometrics on a smartphone will further protect the login process.
As for the flagship Smart Antenna technology, it will fully reveal itself in difficult conditions, in rooms with a large number of people and intermittent interference. High bandwidth, the ability of the antenna to "target" the user and adjust to external interference-these are the functions for which it makes sense to install the WAX650S in the most complex, busiest rooms.
Mikhail Degtjarev (aka LIKE OFF)
18/08.2021