What kind of protection against hackers and forensic experts are there in laptops? We show by the example of Maibenben P415
Many "security officers" do not pay due attention to the laptop hardware, considering that security is limited at the level of antivirus, group policies and automatic software updates. However, in this article, using the example of the Maibenben P415 laptop, I will show you how an ordinary office laptop at the hardware level can be protected from various kinds of attacks, especially those related to the seizure or theft of the device. I do not urge you to go and buy Maibenben P415, but I want you to take a close look at your corporate laptops after reading this article and answer yourself – what of the above do you have?

The most interesting thing is that the Maibenben P415 is not positioned as a laptop protected from IT threats – it is an ordinary ultra-compact machine, and even inexpensive by laptop standards, but this combination of circumstances once again confirms that quite by chance you can find a very interesting device in the portfolio of a company that does not woo itself into the Enterprise world.
Target – memory attack
Everyone who values their data begins protection with disk encryption, fortunately both Linux and Windows have built-in tools for this (LUKS and Bitlocker), so as soon as the laptop falls into the hands of a hacker or a forensic expert, he will first try to access the memory to by making a dump and running a forcic scanner ( for example from the company Belkasoft), extract passwords, including to the encrypted volume, as well as any other important information. If successful, the attacker will receive saved sessions to web services (corporate cloud, email) and any files on disk. If the laptop is locked and invites you to enter a password, there are two types of attacks to gain access to memory.
Problematic: Cold Boot attack is a nightmare of any security person
It has become a nightmare because there is no protection against it (see detailed description in Wikipedia). The essence of the problem is that at low temperatures, even after a power outage, the data in the RAM chips is stored long enough for a forensic expert or hacker to have time to rearrange the memory to another computer, download a special OS image and drain the contents of the memory to a flash drive for subsequent analysis. Moreover, it is not necessary to freeze the chips with liquid nitrogen to absolute zero: as practice shows, a can of spray cooling to near zero degrees Celsius is enough. You can watch an example of such an attack in the video below:
Neither hardware scrambling of DDR4 nor obfuscation provide effective protection against this kind of attacks – only the physical inability to remove the memory modules from the laptop. This was partly confirmed by Microsoft itself, explaining the security requirements of the tightly sealed chips in its Surface laptop (news source).
Solution: using a non-disassembled CPU+RAM+LAN+WiFi module
In this regard, the Maibenben P415 is much more interesting than the Microsoft Surface – here both memory and processor, and even Wi-Fi and LAN controllers are built into one common Intel BKCM11EBI38W board (NUC11 platform), made in the form of a cartridge, which is a single unit, and it can be changed, but it cannot be pulled out of he has memory.
Look – here the cartridge is installed chips down, and removing the laptop cover, pour liquid nitrogen or spray the memory will not work. But even if a hacker pours coolant on the cooler radiators to freeze the entire computing module, he will face another problem – the cartridge is covered with a thick aluminum plate that quickly gives off heat.
I couldn't disassemble this cartridge: I don't know if the screws with which the plate is tightened are soldered or some kind of super-strong thread retainer is used, but chrome-molybdenum screwdrivers simply licked the slots, and the thread did not go. But even if you manage to remove this plate by drilling out the screws (I remind you that in the process of this work you can not turn off the power to the laptop electronics in any way) – DRAM chips will not be able to solder without heating, and do this with cold"attack is not allowed. That's it, the question is closed.
The problem is the possibility of a DMA attack via the Thunderbolt port
The Thunderbolt interface develops high speed due to direct access to memory, but this made it vulnerable to various DMA attacks. Their essence boiled down to the fact that a hacker or a criminologist could gain access to the contents of the RAM of a laptop in a locked state by simply connecting a malicious device to the Thunderbolt or CFexpress port ( see description on the website Microsoft), which introduced malicious code into the OS or dumped memory on itself. The attack itself took several minutes, left almost no traces, and the owner of the laptop did not even know that it took place.
Solution: using Thunderbolt 4 with core DMA protection
Maibenben P415 uses Thunderbolt version 4, a prerequisite for the implementation of which was support for Intel VT-d (see news source), virtualization technology that provides isolation of memory areas at the hardware level. Windows 11 uses two types of protection against DMA attacks: DMA Remapping (for Thunderbolt 3) and DMA core protection based on IOMMU, which is implemented in Thunderbolt 4. This protection is implemented in the following editions of Windows:
- Professional
- Enterprise
- For educational institutions
The status of protection against DMA attacks can be viewed in the system utility "system information", and as we see in the screenshots, Thunderbolt is completely harmless here, since Windows 11 Professional is installed on Maibenben. If your laptop uses Windows 10/11 version "Home" - you are at risk.
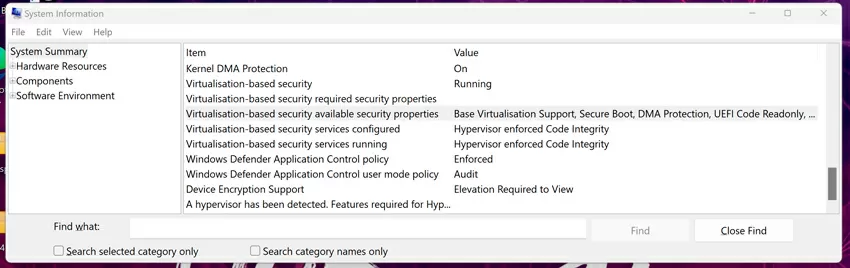
Another thing is that no self-respecting security person will allow you to operate a laptop with an external port that has DMA access, even if it is considered safe, so you can simply disable the Thunderbolt port in the laptop's BIOS, especially if there is no daily need for it.
Problematic – neural networks have learned to recognize a password by the sound of buttons
Each button on the keyboard has its own distinctive sound that distinguishes it from other buttons, a kind of "handwriting" (see original message about an attack). This type of attack is scary because, unlike keyloggers, it cannot be detected by antivirus tools, and a nearby smartphone or the microphone of the laptop itself can act as an eavesdropping device during a phone call, not to mention specially prepared mirkophones in surveillance cameras. For this attack, the complexity and length of the password do not matter, and it is not necessary to have an acoustic cast of the attacked clave – just listen to it for a few minutes, and the recognition accuracy will be 95%.
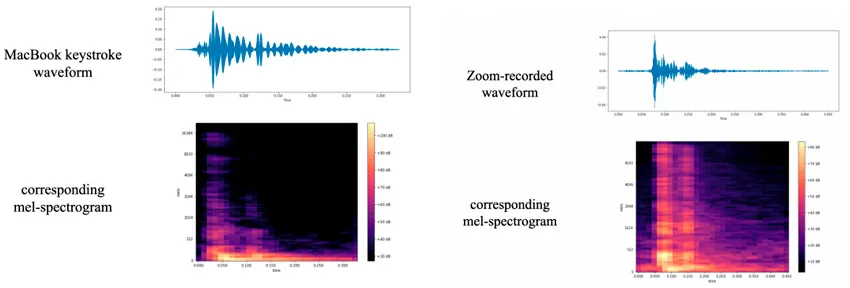
By the way, there is a similar attack on thermal fingerprints on the keys, but it is more complicated than simple listening.
Solution: using a fingerprint scanner and Windows Hello
To protect against this type of attack, as well as from keyloggers and simple peeping at the keyboard using a hidden camera, biometric authorization using Windows Hello using an infrared camera or fingerprint scanner is used. That is, to log in to Windows, you do not need to enter a password on the keyboard. Yes, we have been using all this for many years to unlock smartphones, so everything is very clear here, except that the camera in laptops is put special, RGB + infrared, and in the specifications of the Maibenben P415, like thousands of other laptops, compatibility with Windows Hello is directly indicated. There are proven cases of cheating the laptop's IR camera to unlock Windows Hello using an IR fingerprint (see news), so we do not consider the method of authorization by a person.
But fingerprint scanners are a much more reliable means of authentication, and what's nice is that you can add several fingers, plus an emergency PIN. There are no reliable means of deceiving fingerprint scanners, they do quite well with sweaty hands and dirty ones, and if authentication fails, you will be asked to enter a PIN code. In the Maibenben P415, the fingerprint scanner stands to the right of the touchpad, there are laptops on which it is combined with a touchpad or switch, whichever is more convenient.
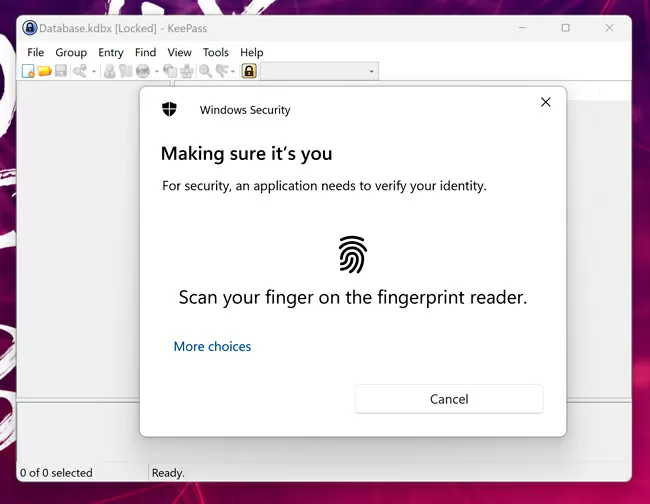
The most interesting thing is that Windows Hello (both fingerprint scanner and face unlock) integrates into other applications that require password entry via the API. Among the most useful such programs is the popular free offline password manager Keepass. By downloading and installing the corresponding plugin (please note that here we are talking about open source software, you can check the legitimacy of which yourself), you can unlock the password database using a fingerprint scanner, and by installing a special extension for the browser, log in to sites "silently" without entering a password on the keyboard.
There is, of course, a more severe option - to use an on-screen keyboard, since the display in the Maibenben P415 is touch-sensitive, but I do not recommend this method, since a fingerprint scanner with a password manager is simpler, more convenient and protected from peeping.
Problematic: Wi-Fi networks suddenly turned out to be unsafe
In 2017-2018, researchers found out that the 4-way confirmation method implemented in the WPA2 algorithm of wireless networks can be hacked and is not secure. Some patches covering the "holes" of the KRAKS attack (see description), have been implemented, but so far an attacker can intercept the WPA2 confirmation, take this information offline and use a computer program to compare it with a list of probable codes in order to find one that is logically consistent with the available confirmation data. Modern bruteforce attacks are often carried out on cloud services with GPU and FPGA boards (see report), so the attackers are not limited by technical means - now it's more a matter of money than time.
What is especially unpleasant in WPA2 is that this protocol allows an attacker to save an encrypted traffic broadcast, and if he is sure that valuable information was contained there, then he can safely go through password options in the Amazon, Google or any other cloud for months, because when he picks up a password, then it will be able to decrypt all traffic and get access to important information inside.
Solution – using WPA3
The WPA3 protocol eliminates the main vulnerabilities of WPA2, making offline password brute force attacks impossible and eliminating the dependence of the security level on the complexity of the password to the WiFi network. But it is worth bearing in mind that it will still be unacceptable to use easily guessed passwords, such as "admin", "12345678". The new SAE simultaneous authentication method does not use a pre-shared PSK key, so it is impossible to hack networks with WPA3 by simply going through the password options offline, that is, without attracting attention. In addition, in WPA3-Personal mode, individual encryption is provided, which does not allow users to track someone else's traffic, even if they have a password and successfully connect to a WiFi network.
But there is one difficulty: WPA3 is not supported by all network cards in laptops. You can often find good inexpensive laptops on sale with an Intel Wireless-AC 7265 network controller – its speed is enough for any task, but only in the list of compatibility with WPA3 (see description on Intel's website) it's not there. Here is a list of network controllers that you need to work with WPA3:
- Intel Wi-Fi 6E AX411
- Intel Wi-Fi 6E AX211
- Intel Wi-Fi 6E AX210
- Intel Wi-Fi 6 (Gig+) Desktop Kit
- Intel Wi-Fi 6 AX201
- Intel Wi-Fi 6 AX200
- Intel Wireless-AC 9560
- Intel Wireless-AC 9462
- Intel Wireless-AC 9461
- Intel Wireless-AC 9260
The Maibenben P415 laptop uses Intel AX201 with Wi-Fi 6 support, so it is ready for a general upgrade of the corporate network to a more secure WPA3 standard.
Problematic: Disk encryption is prohibited in your country
If the data on the laptop can become evidence in the case, and the disk is encrypted, a representative of the law can easily make an unambiguous offer to the owner of the laptop: either you disclose the password and cooperate with the investigation, or you go under the article for using unlicensed cryptography. Encryption may simply be prohibited due to the requirements of the company's policy or due to upcoming changes in legislation. The question arises, how to ensure the safety of data during the seizure or theft of a laptop?
Solution: TCG Pyrite is like encryption, only without encryption
You've all heard about self-encrypting SSD and HDD drives (see Wikipedia article). In them, encryption is implemented by means of the controller of the drive itself, and unlocking is performed at the time of booting the computer by means of the BIOS. The specification of SED-disk protection was developed by the non-profit organization Trusted Computing Group (TCG), and the main emphasis there is on cryptographic protection in the Opal specification, and for countries with strict legislation in the field of encryption, the Pyrite specification has been adopted, implementing the lock of the drive without data encryption ( see detailed documentation in English. and simpler by Opal in English ). The mechanism works by analogy with how it was in old ATA drives and was called "HDD Password". The essence of protection is that the controller blocks access to the storage space until the password is entered, which is set in the BIOS and nothing else. The password never gets into the computer's RAM and cannot be extracted by methods of attacking the DMA core, memory dump or Trojan injection, so it is impossible to hack SED drives. But how, then, can Pyrite without encryption provide protection when a laptop falls into someone else's expert hands? No, I'm not crazy – now you'll understand everything for yourself.
The fact is that access is blocked at the level of the drive controller, whether SSD or HDD. What would a forensic expert do if there was a simple access password on the disk? He would conduct an examination by a destructive method: he would change the controller or take a cast of data directly from HDD pancakes or NAND SSD chips, because the data is stored there in an unprotected form. But the fact is that Maibenben has a 1-chip NVMe SSD Kioxia series BG4, in which there are no memory chips at all!
The NAND cells here are built into the controller itself, and there is nothing to solder out, respectively, it is impossible to conduct such an examination. Neither resetting nor flashing the BIOS will help, and when the SSD is moved to another computer, it will continue to require a password.

Therefore, in this case, although encryption is not used, but the level of protection is the same as in SED disks, and no laws are violated. If the SSD was classic, with a controller and separate memory chips - yes, it would be worse, but otherwise - bingo!
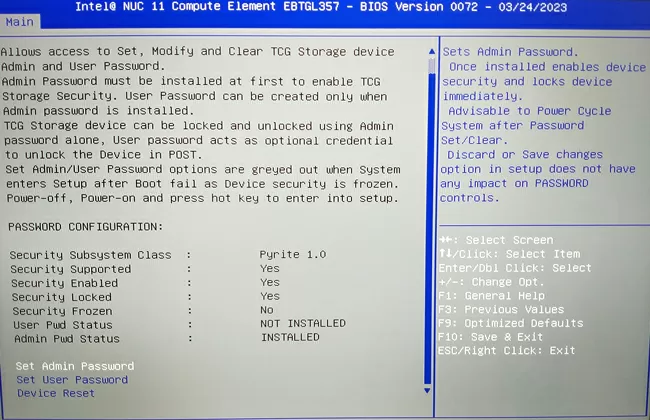
There is, however, one problem: if you forgot your password, you can restore the disk by entering the PSID string, which is usually indicated on the main sticker of the drive, while the data on it is lost. So, in the TCG Pyrite v.1 specifications, unblocking unencrypted Pyrite disks is prohibited, since they do not have built-in information cleaning tools, unlike SED disks with encryption, where after entering the PSID string, an analog of the Secure Erase procedure occurs (see an article about disk cleanup methods). Data cleaning in Pyrite appeared starting with the SCC 2.0 specification in 2018, and in the BIOS of the Maibenben P415 laptop there is an emergency unlock point using PSID, selecting which you will see a warning that in this case all information from the drive will be erased. It turns out that there should not be an unblocking, but there is one.
The TCG documentation states that the manufacturers of drives in the issue of forced cleaning when restoring access to the disk can depart from the official specification and set their own algorithm for deleting data in case of an emergency reset of the drive. I suspect that Pyrite SCC 2.0 is still used in Maibenben P415, and there is an error in the BIOS version, or Kioxia enabled mandatory cleaning at the firmware level in BG4 drives and did not report it anywhere. In any case, if you record, photograph or save the PSID string from the SSD sticker in a conditional place, and then damage it/paint over / tear off, then you can not be afraid for the safety of the data - no one will ever restore them without you.
Finally
Today, all modern laptops have the function of disabling the camera to protect against peeping. In some models, this is a power switch on the case, in some - a folding camera.
In the Maibenben P415, a bright-colored movable shutter is installed in front of the lens, and you can always see that your camera is closed and if she wants to peek, she won't see anything, although this applies more to privacy protection than security.
Conclusions
Modern laptops can become an impregnable fortress for the most terrible scenarios when they fall into the wrong hands or a targeted operation is being conducted against them in order to steal data. What I saw in Maibenben P415 and showed you with examples is not the pinnacle of possibilities, but what you should demand from your laptop vendor if you are at risk or just value your data. Why Maibenben P415 implements such a high degree of protection – I do not know, and I do not want to know, if they said that they supply their machines to the CIA and the Mi6, I would believe it. It is much more important that 99% of laptops on the market do not have such a level of protection, and a competent forensic expert will open them faster than the liquid nitrogen in his mug will evaporate.
Michael Degtjarev (aka LIKE OFF)
27/10.2023