Orchestration of wireless networks in Zyxel Nebula CC: configuring horizontal traffic protection and shaping
Modern networks are gradually changing the traditional topology, in which a security gateway was installed on top, and the network was segmented at L2/L3 levels using switches from below. The modern network is gradually moving towards the concept of Zero Trust, in which only those resources that are necessary for work are available to each device and each application. This reduces the spread of the attack on the horizontal level, if the malicious device is already on the network, and using the Firewall inside the network segment is pointless. To implement such a topology, it is necessary that each connection to the network is broadcast immediately to the security gateway, on which the access rules and user restrictions are prescribed. Figuratively speaking, even a client authenticated on the network should at least sit in his VLAN and access network resources not directly, but through the gateway, having passed all the necessary checks.
If the network is small, the head gateway will quite cope with customer service, but if the network is geographically distributed in different regions, and LTE is used in some areas, then it is more reasonable to take part of the filtering functions directly to the access level so that the already cleared traffic enters the LTE channel, and in case of an incident, it could be closed holes at the branch level, without disrupting the entire infrastructure. For modern wireless Wi-Fi networks, this concept is implemented by taking out security and filtering tools directly to the access point. All clients connected via Wi-Fi are behind NAT, they can pass 2-factor authentication, work in individual VLANs and even access Internet sites through a system of strict rules and restrictions.
Additionally, the client's wireless connection itself can be protected with an individual encryption key, and authentication can be confirmed through a cloud service, which will make attempts to steal the Wi-Fi access key useless.
Let's see how such functionality is implemented in top Zyxel access points managed through the Nebula Control Center cloud service. In this article, I will take the WAX510D point and show you how to configure security settings for clients on it. I just want to draw attention to the fact that the network should be built on such "smart" Zyxel access points (for today it is:
- NWA110AX
- NWA210AX
- WAX510D
- WAX610D
- WAX630S
- WAX650S,
in the future, the list will expand), and moreover, licenses will be required for some of the functionality, CNP+ for application patrol and IP filter, Nebula Pro for dynamic VLAN and DPPSK. NAT, for example, and 2FA are available in the basic version. A 30-day trial period is available for new accounts, during which you can evaluate the work of these functions yourself.
So, traditionally, we start by adding our devices to the Nebula Control Center: the GS1915-8EP switch (which we considered earlier in the review) and the WAX510D access point. For a new organization, we will be asked to activate the trial period of Nebula Pro licenses (entirely for the organization) and CNPC (for the access point). After updating the firmware, go to the wireless network settings.
User registration
In the Nebula tree hierarchy, you have an organization that has several locations, each of which has several wireless networks. Everything related to user names and their personal settings (VLAN number, authorization type) is set globally for the entire organization with an indication of available sites or locally on the site itself, and everything related to wireless connection security settings is set at the level of the wireless network itself, or rather at the SSID level and operates only within the location where the desired wireless network is deployed.
I would recommend companies that are just starting to use Nebula Control Center to create user accounts right away, and although it seems like something superfluous, because ordinary Wi-Fi networks work by password, and do not require any accounts, then you just need to understand that today the industry is moving towards granular configuration of policies and restrictions for each user, and the sooner you join the trend, the easier it will be to operate the network in the future.
Configuring NAT for individual SSIDs
And here the potential of modern WAX510D access points is fully realized: you have one SSID that can work in bridge mode with the internal IP address of the network, another SSID that can simultaneously work in router mode, placing clients behind NAT, the third SSID can connect each client to its VLAN, the fourth SSID - it can be a direct channel via VPN to the headquarters (Secure WiFi technology, which we wrote about earlier), and all these wireless networks can coexist on the same access point and work simultaneously.
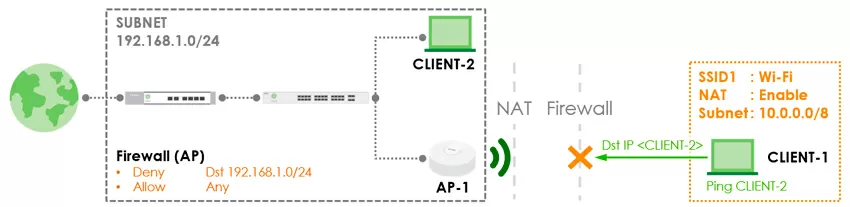
The DHCP parameters are not configured, the access point simply checks the availability of the 10.0.0.0/8 and 172.16.0.0/12 ranges in the network and selects one of them, and subsequently this address is saved even when roaming between access points within the same SSID. And to enable the Firewall, it is necessary to switch the SSID to guest mode with isolation of clients from each other, then the basic rules of the form "block or allow CIDR" will become available. Firewall rules only apply to traffic in the direction of WLAN to LAN, and by default, clients are denied access to private subnets. It should be noted that when switching the SSID to router mode, isolation at the L2 level does not work, because this is quite natural - it is replaced by the L3 level. Also, in this mode, the assignment of an individual VLAN for SID, a custom VLAN for users is not available, and fast roaming according to the 802.11r standard is not supported.
It makes sense to include NAT for guest and IoT devices, that is, for those who do not need access to the local network to perform work tasks. To block the ranges of local networks, the capabilities of the built-in Firewall of access points will be sufficient, and again it should be understood that you do not set this barrier for access from the Internet, but for access from client devices, so some advanced packet processing functionality is not required here.
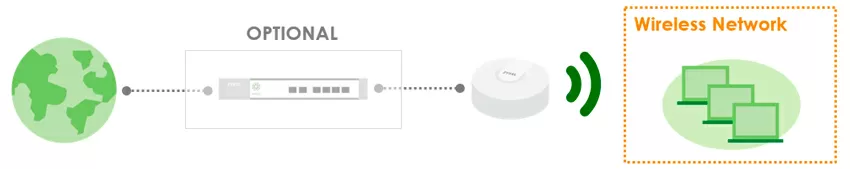
There is another obvious plus that the router mode for access points gives: if the Internet provider gives you access without authorization, you can do with only one access point on some objects, abandoning the switch and router, which means greatly reducing your equipment costs.
Application Patrol
The whole idyll of flexible wireless network settings is violated by the application patrol and reputation filter, - security functions that are applied to all wireless networks of the site at once, without individual SSID configuration. Moreover, well, I would understand if Zyxel had allocated them to a separate top category, and not kept them inside the "access points". After all, the same filters exist in security gateways (see our review), and they do not overlap in any way with those implemented in access points. That is, if you want to use a reputation filter in a mono-brand network based on the Zyxel ATP800 and WAX510D access points, then you will configure it separately on both the gateway and the wireless network. Uncomfortable, what can I say...
The patrol of applications in wireless networks allows you to limit the speed for certain categories of traffic and build appropriate schedules. All restrictions are implemented for groups, for example, for "Telephony/VoIP", and individual configuration of applications and services is not provided. The speed limit applies to each client device.
Reputation filter
A reputation filter acts to completely prohibit access to resources. First of all, I want to specify that we are talking about filtering IP addresses, not domain names. Here, similarly to the previous paragraph, you can select only categories that are closed to all wireless clients, for example, phishing sites, Tor gateways or sites from a personal list (added manually by IP or CIDR). When trying to access them, the client is redirected to a stub with information about the ban, and the event is logged.
Both of the above-mentioned filters are in Beta, and do not even pretend to replace full-fledged security gateways like the same Zyxel ATP800, but act as a useful addition.
DPPSK
Let's consider an equally interesting function related to security: This is connecting users to Wi-Fi using individual encryption keys. Usually, in home or guest networks, all users have one SSID with one password, which allows attacks on the Wi-Fi password to decrypt the intercepted traffic. This is especially true in networks with guest access, for example in hotels, restaurants or other public places, where clients cannot connect using WPA-Enterprise and authenticate through a RADIUS server. Zyxel has a solution ready for such cases, which is a cross between WPA2 and WPAx-Enterprise.
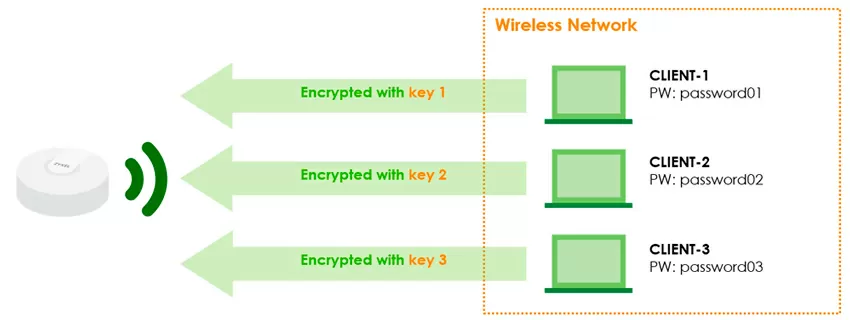
Its essence is that to access Wi-Fi, a key is used that is generated by each user of the organization on the Nebula Control Center portal, it can have a limited validity period and be backed up by 2-factor authentication by E-Mail.
When connecting to Wi-Fi, the user does not specify a common SSID password, but his own, so his wireless channel is encrypted with an individual key, and is reliably protected from interception. Please note: you can set a DPPSK password when creating a user in Nebula Control Center, or you can simply generate only the passwords themselves in batch mode, up to 20 pieces at a time and send them to the mail or print them out. That is, to access Wi-Fi via DPPSK, it is not at all necessary for the user to be registered on the portal.
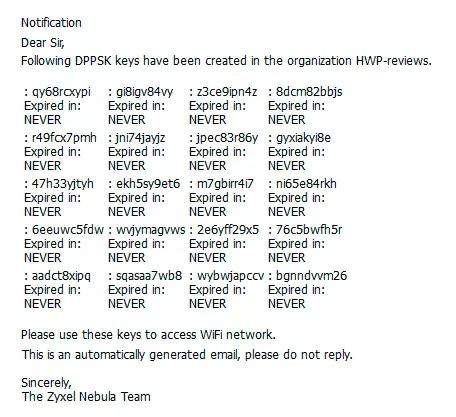
Here everything is the same as with regular Wi-Fi, the client does not even know that he uses one Wi-Fi password, and the neighbor has another. In the Nebula interface, there will be a corresponding mark next to wireless clients connected using DPPSK, and by the way, Zyxel releases an API for working with this function for simplified integration into existing business processes. For example, it will be possible to send a Wi-Fi key to hotel guests at check-in via E-Mail or Telegram.
But in general, it is possible to establish a higher level of security for company employees than for guests by enabling 2-factor authentication for them. It works as follows: to access Wi-Fi, it is not enough just to enter a password: as soon as you do this, you will go to the next stage of identity verification, and here you will need to enter the username and code. You can also authenticate through third-party services, including Google and Facebook. We talked in detail about these methods and their configuration in the review of the Zyxel WAX650S access point, so I will not describe the process itself.
Dynamic VLAN
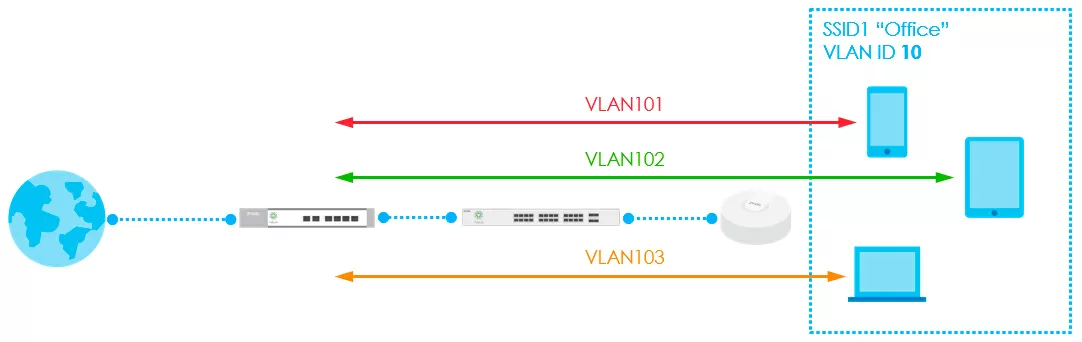
Now I want to touch on an interesting feature of the user's work in different branches of the same corporate network, managed through Nebula. Not so long ago, it became possible to define registered users in their own VLANs for additional isolation. As you can see in the diagram below, the users' own VLANs do not prevent the wireless network from working with its own VLAN, common to those clients whose membership in the virtual network is not defined, or who do not have an account in the Nebula Control Center.
Moreover, a situation may arise when the VLAN ID 101 is allocated for managers in one branch, and the ID 102 in the other. As we remember, user registration in Nebula Control Center is carried out at the organization level, that is, accounts are global for the entire organization. Users can also be created at the site level. The organization level essentially allows you to see all users in the organization across all sites - here you can also add users to all sites at once or to some selective ones.
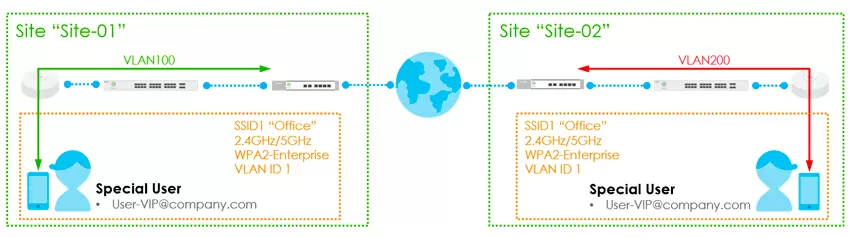
So, now the same user can be assigned different VLANs at different locations, for which you first need to open the "cloud authentication" item from the "Platform" section, select one or more users, and by clicking the VLAN attributes button, assign him a virtual network number.
But here I also have to criticize Zyxel for the lack of user groups and the illogical interface: it turns out that if you have 1 organization and 2 sites, then you will have 3 absolutely identical "cloud authentication" windows: 1 globally for the entire organization and 2 locally, on each site. Why is it so difficult? In order for administrators without full access to the organization to be able to edit users only on certain sites.
Traffic shaping
Zyxel Nebula Control Center has three speed limiting mechanisms for Wi-Fi clients. We have already got acquainted with the first one, which limits the bandwidth for various applications. In addition, there is a global speed limit for each SSID, and inside it you can more accurately shape traffic through VLAN speed limits.
And if you use an individual VLAN for each authorized user, you will be able to fine-tune traffic shaping for each account or application. To make it easier to figure out which shaping method suits you, see the following table:
|
Shape type |
Application Patrol |
SSID |
VLAN |
|
Individual setting for every single SSID |
No |
Yes |
No |
|
Works in NAT mode |
Yes |
Yes |
No |
|
Individual setting for every single user |
No |
No |
Yes |
Nothing prevents you from using all three shapers at once, and it will only be on access points, and you also have speed limiters on the switches and the gateway, so no spikes in your network traffic are scary.
Conclusions
The Zyxel Nebula Control Center cloud management system was created not just to show beautiful graphs of device loading and consumption. Today, it allows you to flexibly manage wireless networks and configure access at the level of users, networks and applications. Taking out some security functions from the gateway to access points can solve potential problems of a surge in traffic and network unavailability, as well as add additional layers of isolation to protect horizontal traffic. I welcome the possibility of installing one access point in some small places of presence (for example, at an order pick-up point), without having to buy a router or switch, but I cannot note that today Zyxel does not have PPPoE authorization on access points in Nebula, so this function will not work with every provider.
As for the disadvantages, it's high time for Zyxel to change the interface of the Nebula control panel: the paths to some settings are already too long, some items are repeated in different places, and the lack of a full-fledged search for functions makes you constantly read the documentation, and that's not why universal control panels are created.
Michael Degtjarev (aka LIKE OFF)
14/09.2022