Quick setup of a wireless network via Zyxel Nebula when deployed in branches
Let's consider a typical case: a large retail chain opens hundreds of new stores, each of which plans to use IoT infrastructure using Wi-Fi 6. In order to facilitate the setup and commissioning of equipment, in other words, so that the sysadmin does not hang around all 100 stores, you can turn the deployment process upside down: first set up the network, and then lay the cables and mount the devices. Today ZyXEL provides you with such an opportunity when using the Nebula service.
Let me briefly remind you that Nebula Control Center is a centralized cloud network controller with which you can configure networks by connecting devices to each other, even without knowing their addresses. We considered a perfect example of such orchestration in an article about setting up various VPN scenarios via Nebula. One of the advantages of using a cloud controller in a complex corporate environment is that you do not touch the rules of Firewall, routing and port forwarding at all, which means you cannot accidentally block devices from accessing the network, after which you will have to reset the device to factory settings. Even if you make a mistake in the rules for LAN, you will always have access to devices via WAN, and you will leave the lion's share of the fuss for your competitors, who configure the network through the CLI or WebUI in the old-fashioned way.
Step 1. Registering devices in the system
So, let's look at a typical scenario in which a company plans to deploy Wi-Fi 6 infrastructure at peripheral facilities. Ideally, the supplier supplies the product with an XML file with a list of device serial numbers, so that it is easier for the buyer to add a large number of devices to the Nebula Control Center, if we are talking about dozens or hundreds of pieces of equipment.
But if such a list is not provided, the system administrator scans the QR code on each package from a smartphone before distributing the equipment to installation groups, adding devices to his organization through the Nebula Control Center application.
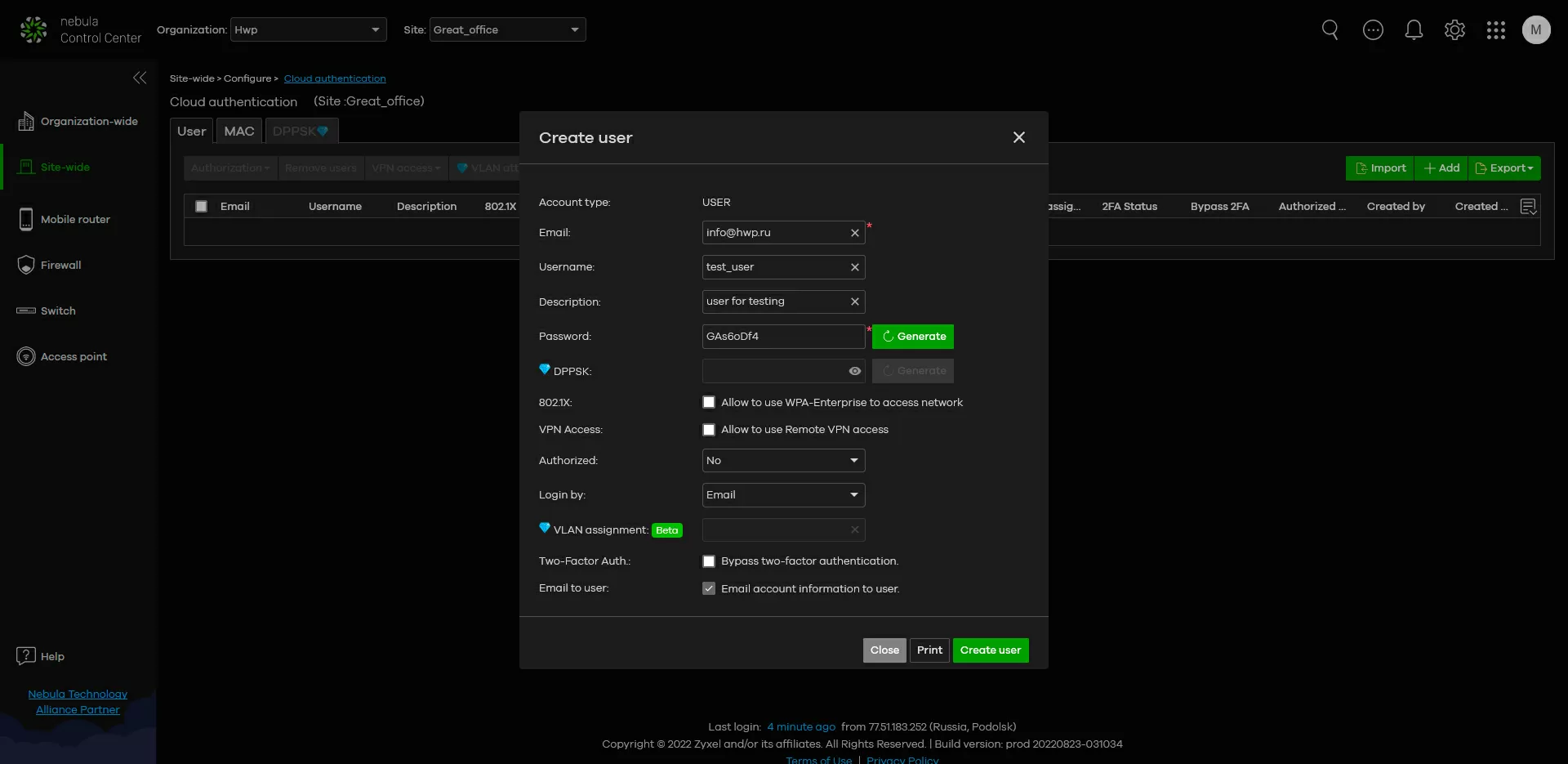
Step 2. Creating Users and Networks
While the new devices are traveling to the places of permanent deployment, you can configure the wireless network parameters for each of the sites in a calm atmosphere. Everything is simple here: for each of the locations, you can set SSIDs, PoE power supply schedule and 2-factor authorization, as we wrote earlier. That is, at each site you can have your own set of users with their own type of authorization in the system.
One of the new functions of Nebula is to allocate each user his own VLAN for maximum isolation from the rest of the network. But, unfortunately, years go by, and there has not been a full-fledged orchestration of virtual networks in the system, so the principle of "one user - one VLAN" is very appropriate here. And you can also create a separate voice VLAN and a virtual network based on Vendor ID.
When purchasing additional licenses, in the "Organization" section, it will be possible to create templates for sites and switches of various models with the necessary port and VLAN settings, in order to then bind them to the necessary switches, automatically assigning them predefined settings.
Zyxel GS1915-8EP gigabit ethernet switch
Today, Zyxel even has entry-level switches that support control via Nebula, and the GS1915-8 EP model is a great example of this. This is a 1-gigabit smart-managed switch with PoE support on each of the 8 ports, designed for mounting Wi-Fi systems and video surveillance networks at small facilities such as a cafe, guest house, car service or a small office. This switch has passive cooling, and can be installed even in the workplace, since it does not take up much space, does not make noise, but at the same time it can serve a network with a total PoE budget of up to 60 watts.
The GS1915 series has models for 8 and 24 ports, with and without PoE support. All switches in this series have the same packet buffer equal to 525 KB and a non-blocking switching matrix with a capacity equal to twice the performance of all ports.
Of the interesting functions, I want to highlight the CPU Protection component, which protects the switch processor from freezes with abnormally high traffic due to DoS attacks or network equipment malfunctions. To work with multicast streams, IGMP Snooping and L2 Multicast are implemented, it is possible to configure priority traffic passing according to the 802.1p standard. LACP is supported for channel aggregation (up to 4 groups), Dual Image technology is used to protect against errors during flashing, and the limited lifetime warranty on the device speaks best about the build quality.
For each of the ports, you can individually set the loop protection algorithm: either STP or the LoopGuard algorithm, capable of responding to loops formed behind the next switch connected to this port. Modern switches support various technologies to reduce power consumption, including scheduled power management, and Zyxel has something to be proud of here.
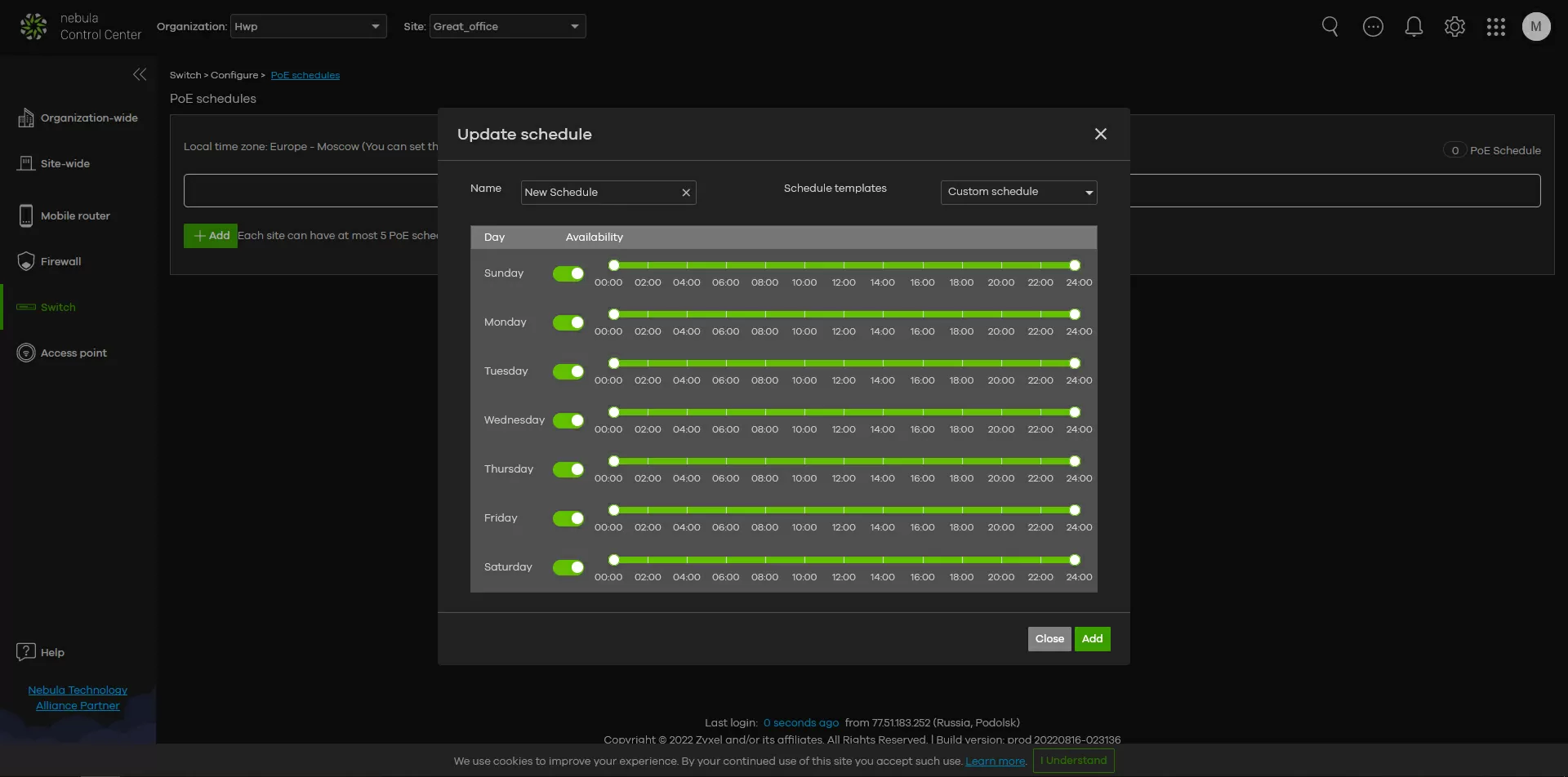
Step 3. PoE
At facilities that do not work in three shifts, a PoE power supply schedule may be useful, and you can attach your own schedule to each switch port. You can manually start the Power Cycle for one or more ports if you need to overload, for example, a hung IP camera.
A cable testing function has been added to each port, and the graphs show how the power consumption has changed over the past 24 hours (when buying a license - up to 30 days). And there is also an interesting possibility of setting the PoE priority for each of the ports. In the case when the total power consumption of the devices exceeds the capabilities of the switch, it will disable ports with lower priority, while maintaining the operability of critical devices.
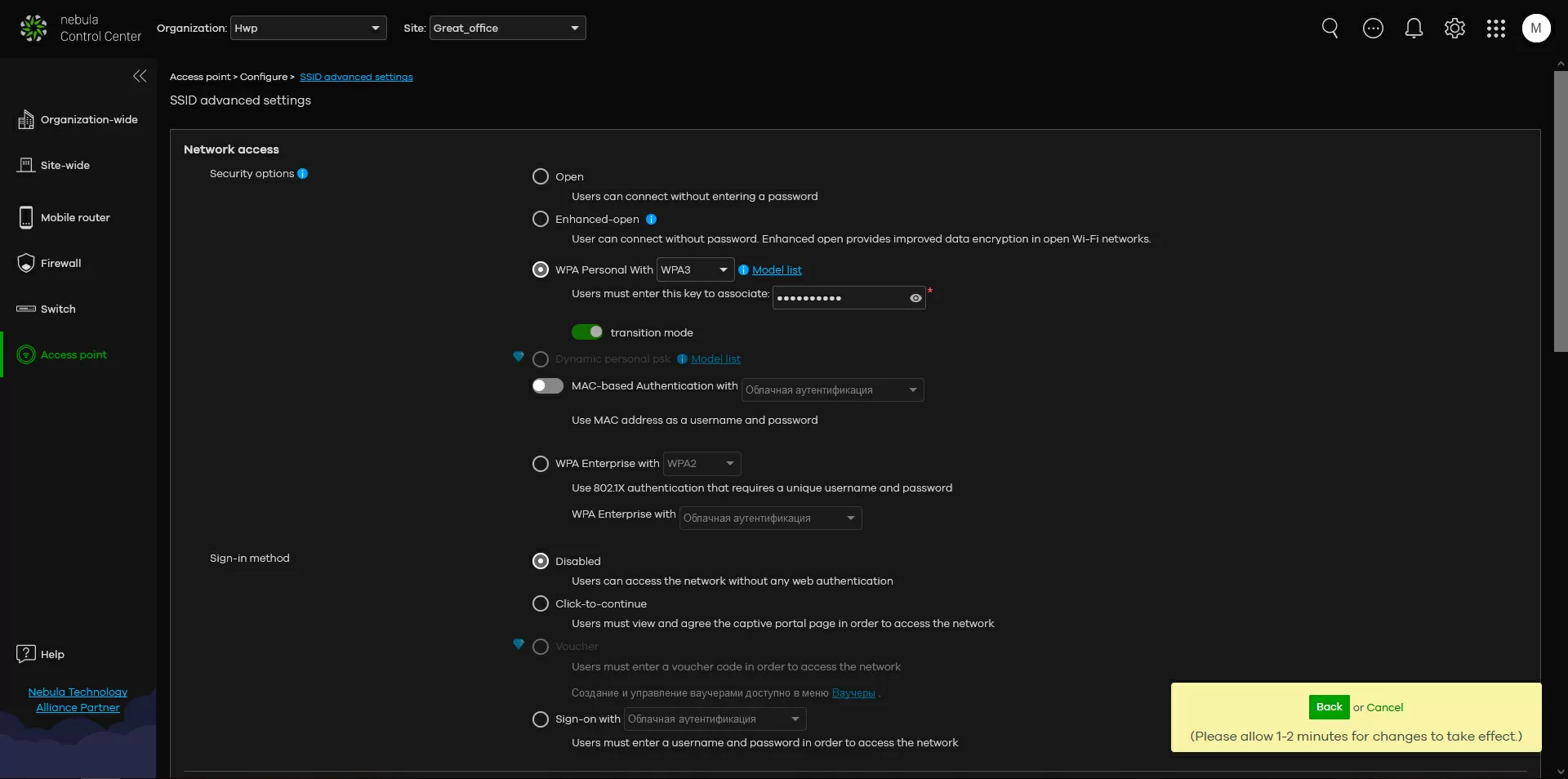
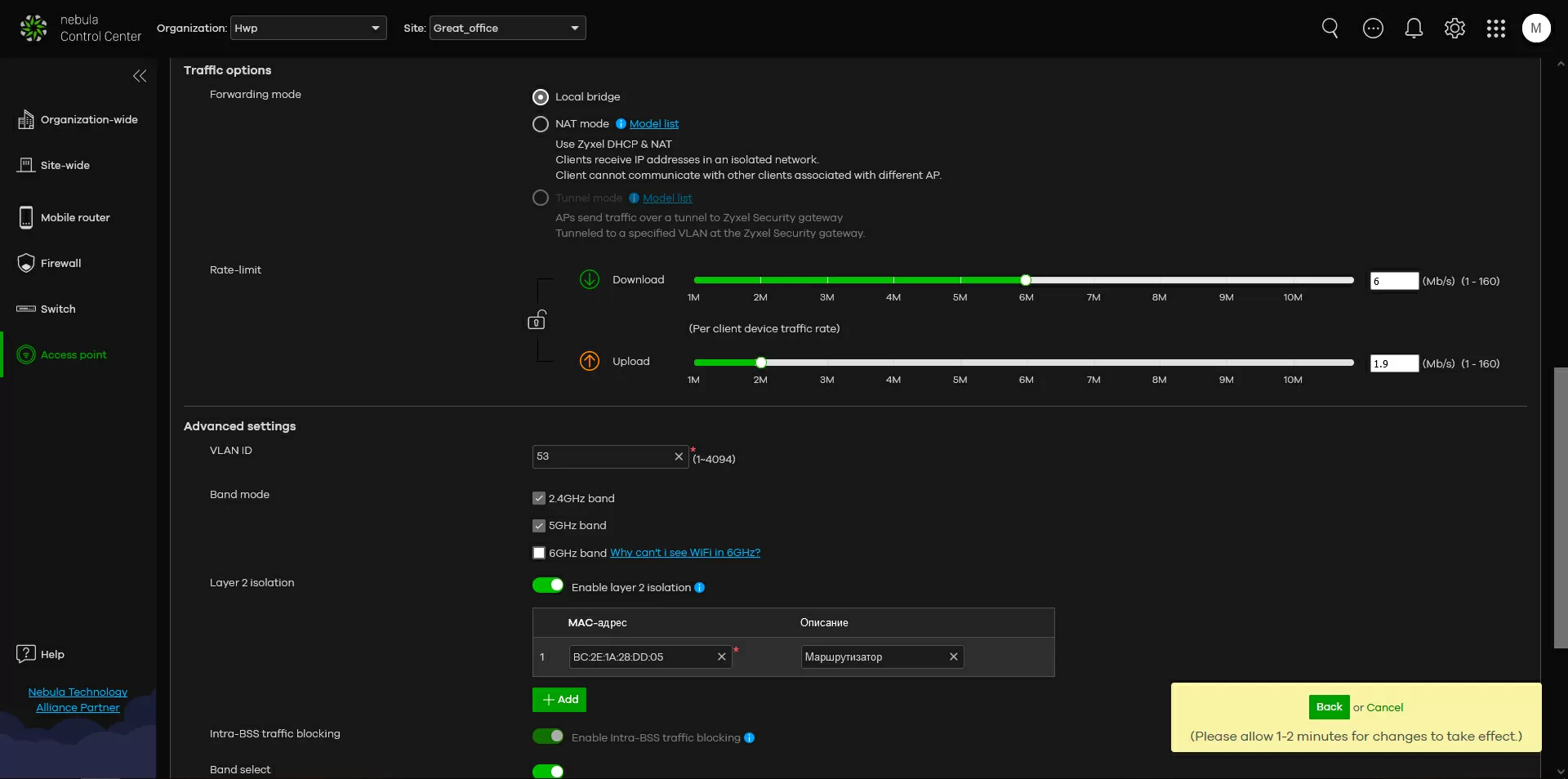
Step 4. Security preferences
Здесь я хочу сделать небольшое отступление и сказать, что сегодня всё чаще какие-то функции безопасности выносятся непосредственно на точки доступа, что позволяет выстраивать дополнительную линию защиты внутри периметра. Ну а что? Процессоры ТД уже достаточно мощные не только для работы NAT, но и для применения различных репутационных фильтров, позволяющих отсекать зловредный трафик не только в момент атаки на сеть, но и когда заражённое устройство пытается получить доступ к подозрительным сайтам. Согласитесь, если IoT датчик постоянно пытается выйти в сеть ToR или стучится на какой-то облачный хостинг, вы захотите не просто об этом знать, а предотвратить такую возможность в принципе. У топовых точек доступа, таких как ZyXEL WAX650S есть встроенные службы безопасности, которые решают проблему защиты внутри периметра по постоянно обновляемым сигнатурам.
Well, to differentiate access at the L2 level, you can simply use several SSIDs with different VLANs, and by setting tags, you can assign different wireless networks to different access points within the same site. In principle, returning to the paragraph above, you can generally enable router mode on some SSIDs, and bridge mode on some, and apply both modes simultaneously to the same access point. As a result, some clients will work for NAT, while others will be connected to the network directly, but again I want to say that not all access points support this mode.
Well, the easiest way is to use isolation at the L2 level through a list of trusted MAC addresses. Here, for example, we can specify only the MAC address of the security gateway and be sure that wireless clients will not get access to any other devices or applications on our network. All their traffic will pass through the internal Firewall.
Please note: everything related to the second level and VLAN is organized at the SSID level, and to restrict access to Internet resources, although it does not work on all access points, it is configured globally for the entire site.
Zyxel NWA90AX
One of the simplest access points with Wi-Fi 6 support, PoE and cloud management, Zyxel has the NWA90AX. This is a ceiling model with support for switching the client between bands (Band Steering), seamless roaming and the ability to work in Mesh networks.
The radio module supports the 2x2 MU-MIMO format, which gives a total speed of 1775 Mbit/s when using the 2.4 and 5 GHz bands simultaneously. The maximum channel width is 80 MHz.
The NWA90AX model has modest gain coefficients in both ranges: 3 dBi for 2.4 GHz and 4 dBi for 5 GHz, the radiation pattern is almost perfectly circular in both horizontal and vertical planes. Based on this, the ideal installation location will be the overlap between the floors, so that the longing covers the space both below and above itself. In cottages and country houses, it makes sense to place NWA90AX under the ceiling of the first floor, then it will cover the second floor.
In general, the NWA90AX is a budget solution for mass installation, and you will not find any interesting features that the more expensive Zyxel models have here. Her main advantage is that she is small, cute, works with Nebula and is inexpensive.
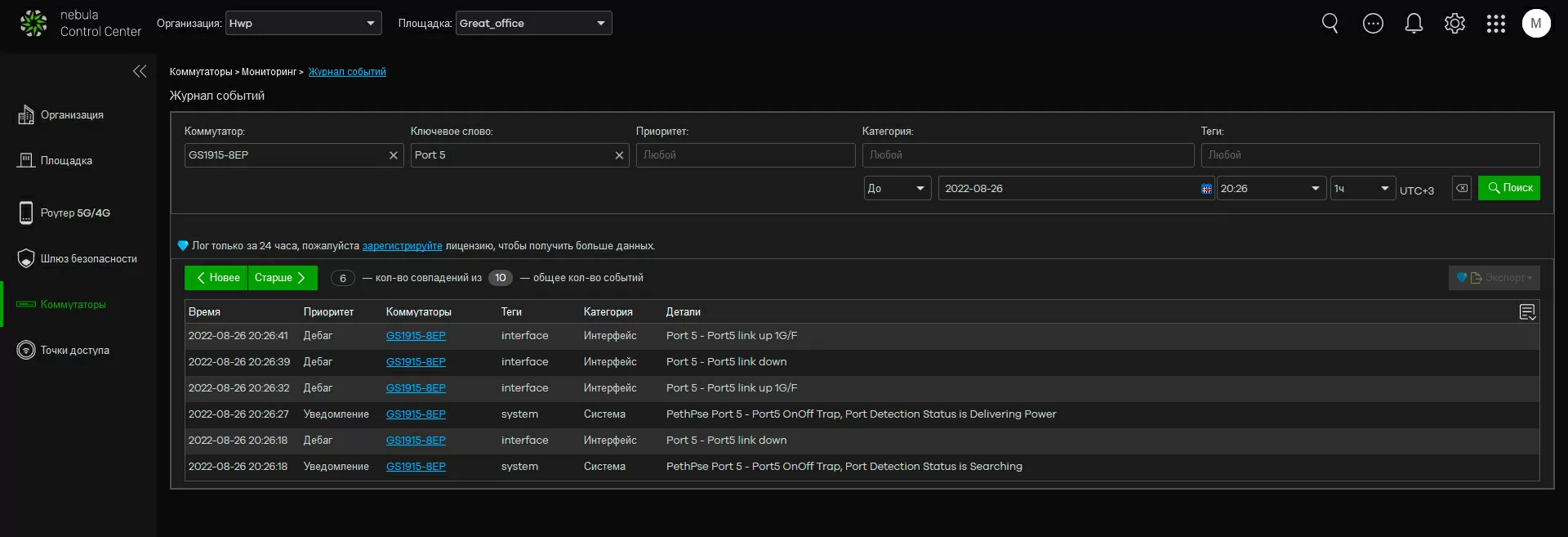
Step 5. Setting up logfiles and alerts
From the point of view of event logging, everything is organized quite interestingly in Nebula: a log is displayed separately for all access points on the site and separately for all switches, plus you can output a common log file for the entire location network. When investigating incidents, keyword search and date range are available to you, which allows you to read logs for each switch port individually (!), but with a basic license, the log is saved only 24 hours, so it makes sense to enable sending the log to your Syslog server in the cloud to monitor the system via ELK, Loki or a similar software stack.
In addition to the logs, you can view summary reports by device class, which will give you an understanding of port loading, PoE device power consumption, access point and wireless network loading, as well as information about the most active applications and clients.
With the basic license, notifications are available to you only through Push notifications, and you will already have to pay for the ability to send messages to E-Mail. As for notifications via Telegram, there is not a word about it. Triggers for triggering alerts are fixed, and there is no provision for creating your own rules for notifications.
Among the available triggers are only those that directly affect the operation of the network, such as "switching devices offline", "adding/removing devices from the site", "connecting/disconnecting WAN" and so on. For some reason, there are no alerts on temperature or errors at the physical level.
Final steps
At this stage, we can say that our network is configured, and the installers at the facilities will only have to fix access points, install switches, compress the twisted pair and turn on the power. As soon as the devices are launched and find Internet access, they will automatically download the configuration from the Nebula cloud, and you will only have to update the firmware with one click for the entire fleet of devices at once, and watch traffic flows in a visually pleasing interface.
A centralized cloud controller will save you from port forwarding settings and providing an extra layer of protection for the control network, so even at facilities operating via LTE and behind NAT, you will retain control over the infrastructure in the same way as if access points and switches were on your desk.
Michael Degtjarev (aka LIKE OFF)
29/08.2022