We explore Zyxel Connect & Protect and answer the main questions: is it possible to do without a security gateway?
No, but really, why should an expensive security gateway be built on a small facility where the network infrastructure is completely wireless? Modern access points have powerful enough processors to take over the processing of traffic and block access to malicious sites, or reduce the speed to various social networks and useless time-killers there. From the point of view of the network, a modern object can be just one access point connected directly to the WAN from the provider, and there are enough resources on this access point to raise the VPN tunnel to the headquarters, and for NAT, and to configure restrictions for clients.
And in such simple cases, when a wireless network is deployed in a small office, in a burger shop, barbershop or car service, security issues are usually taken out of brackets, but the reckoning may not take long.
What typical threats should you prepare for?
The most harmless is the case when employees of an organization, instead of working, spend all their time in social networks and online cinemas, clogging the bandwidth and spending paid traffic.
A more serious problem is downloading malicious software and infecting office computers. As many years ago, the most common reason is the human factor: a click on an unknown link from an unknown sender or an attempt to open an attachment file. Infected computers often become part of a hacker botnet, and along the way, when they try to download part of their code from the Internet to receive instructions, there is a chance to stop their action on network gateways. Similarly, with built-in miners.
Among the more significant problems is the use of a guest network for hacker attacks and access to prohibited content. This is the situation in connection with which the business owner will "definitely come" and "start asking questions", trying to shift responsibility for the incident to him, or in simple terms, to make it extreme.
There are other threats, and as a rule, incidents manifest themselves in a chain, and one pulls the other.
Maximum threat - responsibility before the law for the client or employee
I consider the maximum threat to business to be a violation of the law from your network, that is, the case when your client tried to access a blocked site from a phone via Wi-Fi, the provider's gateway registered it and automatically reported it to law enforcement agencies, at the same time disabling your Internet access. I believe that this is the reality of tomorrow, and you can prepare for it today, and since departments are very sensitive to documents, buying a license to protect traffic from Internet threats, any organization will have a better chance to evade responsibility by blaming the supplier of this protection.
What protection does Zyxel offer for wireless access points
At Zyxel, Internet traffic protection is presented in the form of a service activated through the purchase of a CnP / CnP+ license (stands for Connect and Protect) in the Nebula Control Center service. This service is available only for new models of access points, and as you have already understood, network management must be connected to Nebula (and what happens if Nebula is suddenly blocked on the initiative of the authorities? We found out in our article).
Connect and Protect protects two-way traffic only to dangerous Internet resources such as botnets, phishing sites, anonymizers, Tor proxies and from them towards the client network. If a virus has been introduced to an employee's laptop or smartphone, the CNP system can prevent him from contacting the managing server and replenishing the ranks of botnets, but its main task is still not to allow wireless network clients to visit sites on purpose or accidentally that may be dangerous for both the organization and themselves.
What type of filtering is provided in CNP/CNP+?
Signature-based filtering is the most ancient, and at the same time the most effective way of protection. A database of all dangerous Internet websites is downloaded to the access point (of course, not all, but many), distributed by category, and then each outgoing request is analyzed by DNS header and/or IP address, and either resolved or blocked, displaying the appropriate warning to the user. You can configure the ability to bypass such blocking by giving the user a warning that he goes to the site at his own risk.
The categories of Internet resources themselves are not customized by the administrator in any way: through the web interface there is no way to check the entry of a particular resource into one of the categories, move it to another or check the entire list. Only a whitelist of IP addresses and domain names is available to configure exceptions. If you still need to check whether the IP is in any of the categories, then you can do this via the command line by connecting to the access point to which the CNP/CNP+ license is applied.
How licenses CNP/CNP+ are assigned
Since there can be many access points in an organization, including old ones that do not support Connect n Protect functions, the following filtering scheme is provided in Nebula Control Center: the CnP/CnP+ license is purchased specifically for the access point: you need protection in the meeting room and lobby - please hang CnP on these access points, you do not need in the household.premises - do not buy. Once enabled, CnP immediately covers all the SSIDs available on the access point.
And what is the difference between CNP and CNP+ in general?
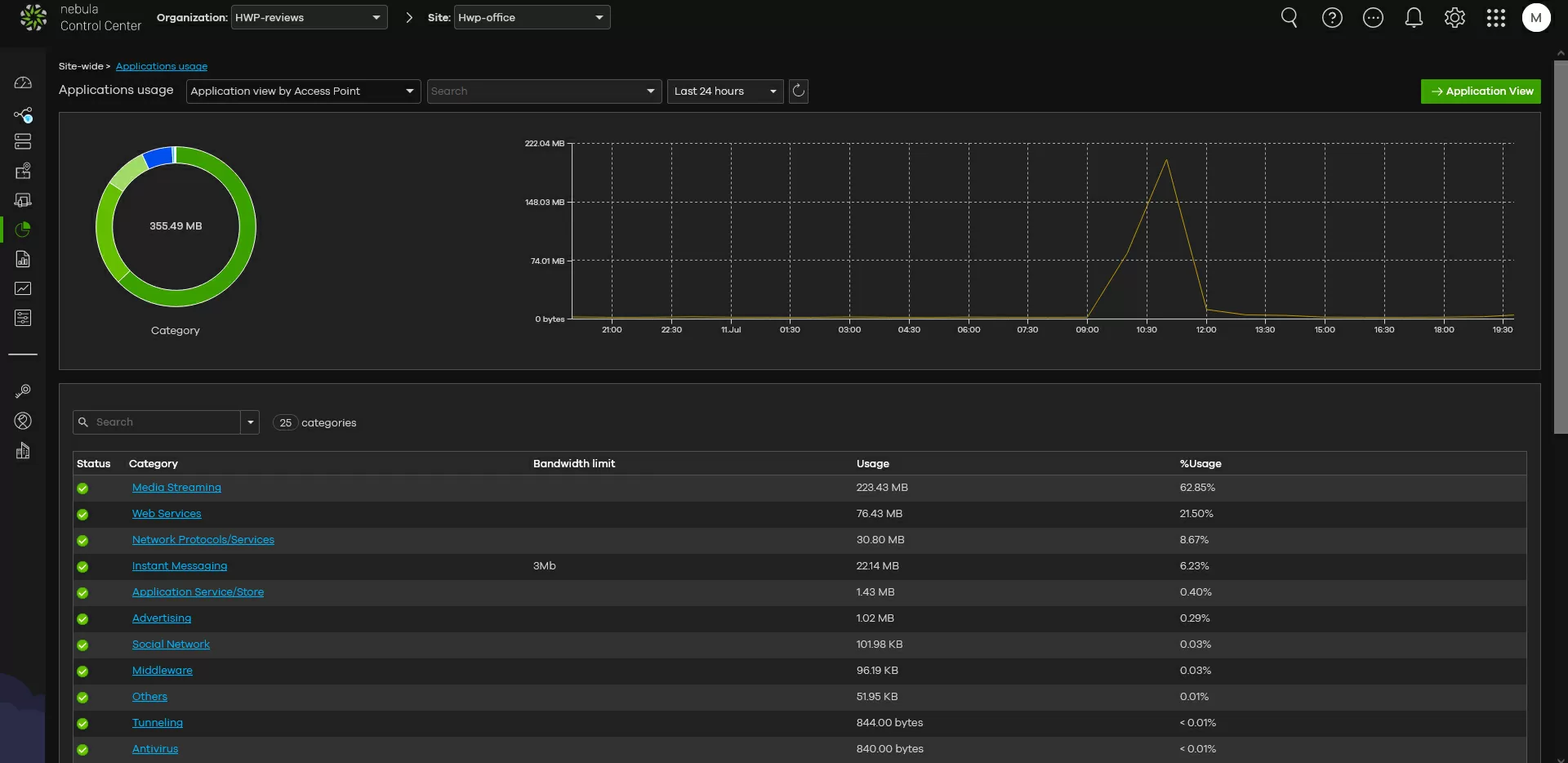
The only significant difference between CNP+ is the bandwidth limitation for some web applications that are detected automatically. In practice, this happens as follows: after enabling CNP for access points, we wait for some time until the device collects network usage statistics and the corresponding entries appear in the "application patrol" column in the interface. By clicking on any of them, we can set a bandwidth limit that is valid individually for each client. I liked that CNP easily identifies messengers, including Telegram, whose channels are filled with videos today and devour traffic no worse than Youtube.
Again, this approach is fraught with drawbacks: it will not work in advance to limit the bandwidth for applications that have not yet appeared on your network, but you can apply restrictions for the category, which will be discussed later.
At the time of writing this article, CNP was supported by the following access points:
- NWA1123ACv3
- WAC500
- WAC500H
The extended version of CNP+ is supported by these models:
- NWA110AX
- NWA210AX
- WAX510D
- WAX610D
- WAX630S
- WAX650S
The nomenclature shows that CNP support is being curtailed in favor of the more advanced CNP+. But the question arises, how will the bandwidth restriction work if there are both old and new access points on the network? Everything is trivial and simple: if the client is connected to a new access point that supports CNP+, then the restrictions will work for him, if they are not connected to the old one.
Is it possible to block access to applications?
Let's repeat once again - the Connect n Protect system closes access only to malicious Internet content, and does not aim to restrict the user's freedom on the network. Therefore, if you want to block Telegram, Reddit or VPN, you will not be able to do it, at least with this function. The maximum that you will be able to do is to reduce the speed to 1 Mbit/s for a single application or the entire category.
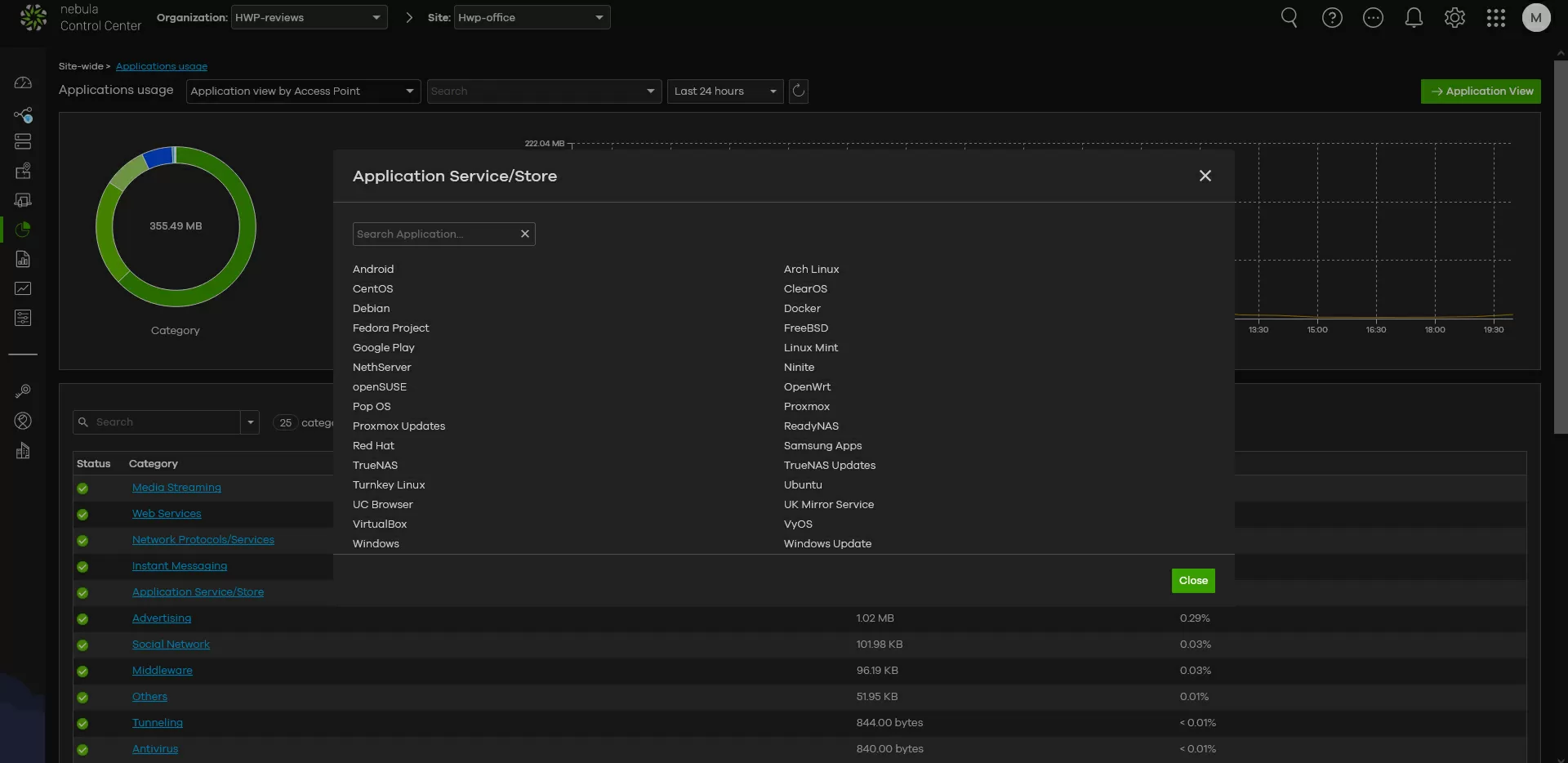
Unlike filtering malicious sites, supported applications can be viewed through the Nebula web interface, for which you need to go to the "Platform - applications" and select "category overview".
Click on the category we are interested in - and see what it includes.
What about blocking VPN?
If the user uses a VPN to access the Internet, then through CNP/CNP+ you can restrict access for the entire VPN tunnel. Naturally, CNP will not be able to look inside the encrypted traffic, and limit the user's work via VPN, too.
Both tunneling protocols (including OpenVPN and Wireguard) and VPN services such as NordVPN and GhostVPN are supported here.
Does an access point with CNP/CNP+ enabled redirect all traffic through Nebula?
No, the access point downloads the signatures of the filtering system from the cloud every day or when connected to the network, and in the future it already operates autonomously, so if the connection with the Nebula Control Center is disrupted, it will not affect the operation.
What statistics are available on the work of CNP/CNP+?
The Nebula CC control panel displays the intensity of wireless network usage: active applications, the number of IP address checks and bandwidth usage for various applications.
To check the distribution of traffic and threats across clients in order to identify a problematic machine or device on which the malware is sitting, you can only view the logs of access points, and this is inconvenient, but I suspect that this restriction is related to compliance with privacy laws, because if such statistics were right in front of the administrator's eyes, he could see which the websites are visited by an unlucky client, and this would entail a violation of the basic rights and freedoms of the poor guy.
So let's go back to the original question and answer, can Zyxel Connect and Protect replace a security gateway in small installations?
In my opinion, if the object on which Wi-Fi is deployed is something like a cafe, a beauty salon or a car service, where one access point is installed, and it is also a router, it is quite possible to do without a security gateway. CnP service will make Internet access a little more secure and will help to unload the radio airwaves if customers abuse free Wi-Fi. Again, for offices for 3-5 people, this is the same simple and affordable option to resist hacking through social engineering: the access point is quite able to protect against clicking on a phishing link received in an unfamiliar letter. The ease with which it is configured is commendable: compared to how difficult it is to set up NGWF, here all security comes down to pressing one button.
But at the same time, it was not without drawbacks: the inability to completely block access to applications personally perplexes me, and reporting on the triggering of filters leaves much to be desired. Therefore, if network security is put in the main priorities, you cannot do without a full-fledged gateway/ NGFW.
Michael Degtjarev (aka LIKE OFF)
13/07.2023