Evolution of cyber threats in OT environments
This year marks 10 years since the discovery Stuxnet. A malicious computer worm hit the headlines because it was targeting supervisory control and data collection systems (SCADA).
Stuxnet's code, large and sophisticated, over 500 kilobytes in size, has managed to infiltrate Windows devices and networks, copying itself several times before looking for additional software. It was aimed at programmable logic controllers (PLCs ), which provide automation of electromechanical processes in machine tools and other industrial equipment.
Since the discovery of Stuxnet, there have been many similarly sophisticated cyber attacks on enterprise management (OT) systems around the world. In part, this may be due to the increasing degree of Internet connectivity of such networks, which makes them more vulnerable to attacks by cybercriminals, governments and hackers. In fact, according to Fortinet research “ State of Operational Technology and Cybersecurity Report ”, 74% of organizations using OT have experienced a malware infection in the past 12 months that harmed productivity, revenue, brand trust, intellectual property, and physical security.
Most Significant Attacks on OT Environments and ICS
By evaluating the most significant cyberattacks against industrial control systems (ICS) in the past decade, we can see how far the technological capabilities of criminals have come. Perhaps even more worrisome, however, is their willingness to harm not only digital infrastructure but also physical infrastructure, negatively affecting individual employees and entire companies. Stuxnet is perhaps one of the first in a series of malicious attacks on ICS to demonstrate to organizations around the world the magnitude of the impact cyberattacks have on physical infrastructure.
The emergence of new mechanisms of threats and attacks radically changed the specifics of the functioning of industrial control systems (ICS) and SCADA. In the following, we list some of the most notable ICS cyberattacks that have occurred over the past decade and describe their impact on current critical infrastructure security strategies.
2011: Duqu
Hungarian cybersecurity researchers discovered malware identified as Duqu, which was very similar in structure and design to Stuxnet. Duqu was designed to steal information by disguising data transfers as normal HTTP traffic and transferring bogus JPG files. A key takeaway from the Duqu discovery was the understanding of the importance of intelligence to criminals - often malicious code to steal information is the first cyber threat in a planned series of additional attacks.
2013: Havex
Havex is a fairly well-known Trojan for remote access (Remote Access Trojan –RAT), first discovered in 2013. Havex, in the GRIZZLY STEPPE threat group, targets ICS systems and communicates with a C2 server that can deploy modular payloads.
Its ICS-specific payload was gathering server information for an open communication platform (OPC), including CLSID, server name, program ID, OPC version, vendor information, execution status, number of groups and server bandwidth, and was capable of counting OPC tags. By interacting with the C2 framework, the Havex malware posed a significant threat in terms of its ability to send instructions that provide advanced and unknown capabilities to the malware.
2015: BlackEnergy
In 2015, it was discovered that BlackEnergy malware was used to use macros in Microsoft Excel documents. The malware infiltrated networks through phishing emails sent to employees. Although the tactics used by these attackers were relatively simple, the event proved that cybercriminals can indeed manipulate critical infrastructure on a large scale.
2017: TRITON
TRITON Malware , discovered in 2017, targeted industrial safety systems. In particular, it pursued the security instrumented system (SIS) by modifying built-in firmware to add malicious functionality. This allowed attackers to read or modify the contents of the memory and activate their own code, along with additional programming to safely shutdown, block, or alter the failover capability of the industrial process. TRITON is the first known malicious software specifically designed to attack industrial security systems that protect human lives.
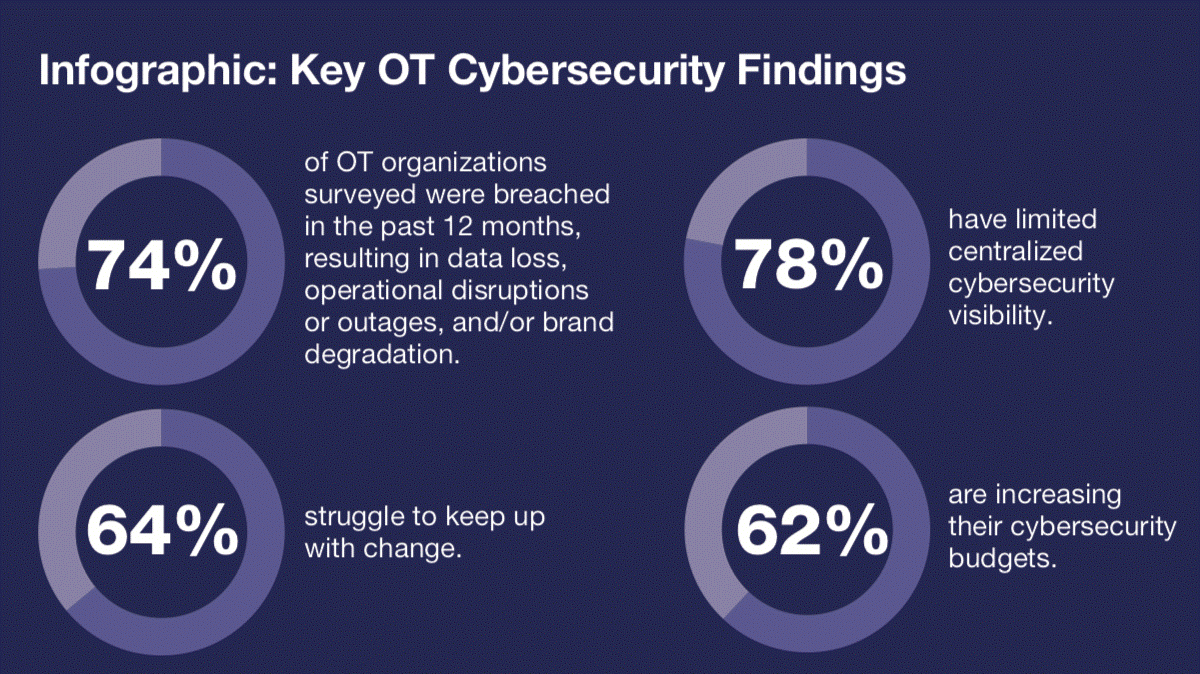
- 74% of organizations surveyed indicated that their OT environments have experienced attacks in the past 12 months, resulting in data loss, business disruption and/or damage to brand reputation.
- 78% of companies surveyed have limited their centralization of cybersecurity visibility.
- 64% find it difficult to keep up with changes.
- 62% increase cybersecurity budgets.
ICS/SCADA Security Troubleshooting
ICS encompasses a large segment of the OT layered architecture that encompasses many different types of devices, systems, controls, and networks that control manufacturing processes. The most common of these are SCADA systems and Distributed Control Systems (DCS).
For many years, most organizations have been implementing measures to ensure information security, but OT security is a somewhat new territory. With the increasing penetration of Industrial Internet of Things (IIoT) technologies and the subsequent convergence of IT/OT, manufacturing lost the “air gap” that protected their OT systems from hackers and malware. As a result, attackers are increasingly targeting OT systems to steal confidential information, interrupt operations, or commit cyber terrorism against critical infrastructure. This is in part because existing malware works effectively against legacy systems deployed on OT networks that have probably not been patched or updated given the lack of additional resources for revision.
A number of challenges have played a role in the evolution cyberattacks that have affected OT systems over the years. Among them:
- Insufficient inventory of OT devices. Organizations cannot protect assets - whether by applying patches or conducting security audits, if they do not have full control over the environment.
- Lack of dial-up access to the network. Most of the technologies underlying ICS are based on limited physical access and hidden components and communication protocols.
- Outdated hardware and software. Many ICS and SCADA systems use outdated hardware or outdated operating systems that are incompatible or too delicate to support modern security technologies. Often such hardware is deployed in environments where systems cannot be shut down for patching or upgrades.
- Poor network segmentation . OT environments tend to operate in full trust settings, a model that does not translate well into new converged IT/OT environments. ICS generally does not use standard security practices for dividing networks into functional segments that limit data and applications that can migrate from one segment to another.
- Limited access control and permission management . As previously isolated or closed systems become interconnected, the controls and processes that enforced access often become confusing.
Fortunately, the risks that lead to security threats to ICS/SCADA are becoming more widely recognized and, as a consequence, more of a priority for many large organizations. Government agencies, including the Control Systems Cyber Emergency Response Team (ICS-CERT) in the United States and the Center for Protection of National Infrastructure (CPNI) in the United Kingdom, are currently issuing guidance and advice regarding using ICS best practices.
The International Society of Automation (ISA) has also developed standards based on the framework "zones and channels ”(Zones and conduits), which addresses the most pressing security flaws in the ICS network and provides recommendations for better governance. Likewise, the non-profit organization ICS-ISAC is focused on sharing knowledge about risks, threats and best practices to help businesses develop situational awareness to support local, national and international security.
Need to maintain critical infrastructure
Due to the potential impact of an attack on the physical security of employees, customers and communities, ICS/SCADA security should be prioritized. It also means that regulatory compliance cannot be ignored. Fortunately, by taking a layered approach to securing digital industrial systems, organizations can dramatically improve their overall security and risk mitigation strategies.
06/26/2020