How Zyxel Secureporter facilitates corporate network security monitoring
Large modern IT vendors strive to earn not only on the sale of hardware, but also on various subscriptions and services, and Zyxel is a clear example of this. Today, the company is actively promoting its cloud-based network stack management system, Nebula Control Center (NCC), to which we have devoted many articles. The service itself is free, and very convenient from the point of view of installing / maintaining networks with branches, but over time Nebula Control Center began to acquire additional paid services, one of which we will talk about today.
Zyxel Secureporter is a single assembly point for reports, dashboards and statistics on the operation of your network's security gateway. Naturally, only Zyxel gateways of the USG Flex and ATP series for small and medium-sized businesses are supported. According to the developers, Sitereporter will allow sysadmins to better investigate and predict traffic anomalies, block unwanted connections and configure security policies more effectively. To check how convenient everything is, let's take the simplest gateway of the NGFW family, Zyxel ATP100, and configure security policies.
Mandatory conditions - connection to Nebula
The Secureporter service is tightly connected to the Nebula Control Center cloud system, and works both with gateways that are managed through the cloud, and with those that are offline, but of course only with Zyxel production models. Today it's all USG Flex and ATP: for some, NCC support immediately at launch, and for others it was added with firmware updates. If you are still not familiar with the capabilities of the Zyxel ATP, then we recommend our review of the top model ATP800. These are full-fledged NGFWs with antivirus scanning, sandbox mode, intrusion prevention systems, content filters, application signatures, HTTPs decryption and much, much more on board. To date, all UTM functions, except SSL Inspection and antispam, are available in Nebula, so the question of the expediency of migrating to the cloud can no longer be raised.
In the logical view of Nebula Control Center, you have organizations and sites where networks are deployed. A site can have only one network gateway, and security policies are set separately for it and NGFW filters are configured. The advantage of cloud control is that here you organize your network and monitor traffic from the gateway to the end device in a single window. If your branches are connected by VPN tunnels, then you will see their topology here, on the map of the area (read the article about the orchestration of VPN tunnels through Zyxel Nebula).
After you have added the Zyxel Internet gateway to the site, go to the portal MyZyxel.com and activate the appropriate license. For ATP, a Gold Security Pack license is used, which includes all subscriptions, including SecuReporter. To make it easier to choose a license specifically for your equipment, Zyxel has a convenient online store with an auto-renewal function. After some time (in our case, a few hours), the site was added to the service. If in the future we want to upgrade a simple ATP100 to ATP500, then all settings and all telemetry will be saved and automatically transferred to the new gateway.
Setting up Security Rules
The logic of NGFW is as follows: first, you need to configure traffic filtering solutions, and then create security policies for the site based on them. This approach allows you to flexibly operate with different ranges of IP addresses and user accounts, fine-tuning filtering and blocking. For example, you can ban any traffic to financial services from Afghanistan (if there are any) on Thursdays at lunch, and not just filter the websites and servers of banks and cryptocurrency exchanges.
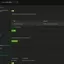
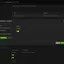
We start by defining content filtering rules for Web surfing. As good examples, we are offered the templates Parental Control and Productivity, and if you do not know which category the desired website belongs to, just enter its address in the appropriate field. Similarly, through AppPatrol, we create a list of messengers that we will block in our network in the future.
Go to the security policy section and create simple and clear rules for restrictions on outgoing traffic in our network.
SecuReporter Security Reports
The complete absence of settings immediately attracts attention: apart from switching the bright/dark theme, there is nothing else: even the language is only English here so far, and localization is expected this year.
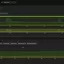
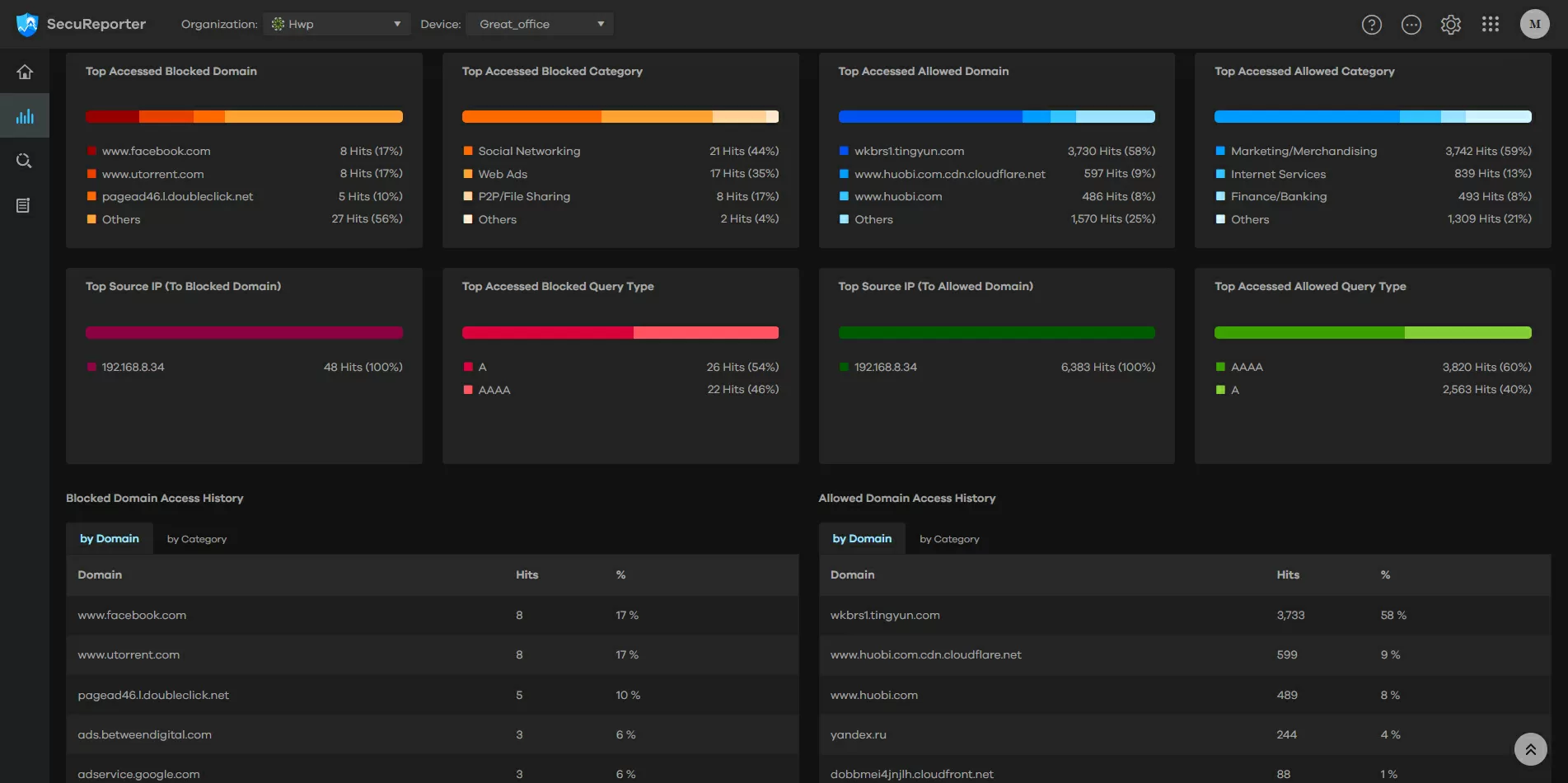
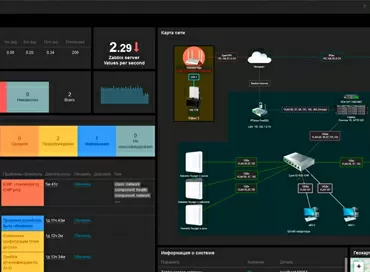
The dashboard displays data for only one site, that is, from one gateway. For some reason, there is no way to see the entire organization at once here. In the right part of the map, which reflects the geographical coordinates of threats. There is no need to pay extra for GoIP - everything is included in the basic gateway subscription.
All information on detected attacks is displayed on the timeline in the form of graphs, between which you can switch tabs. Thus, one glance is enough for the administrator to determine what type of attacks are coming from which regions, and if necessary, simply block the entire problematic country or even the continent if there are no interests of your company there.
What can you use the IP address blocking report for?
Some experts believe that blocking IP addresses has outlived itself, since many unwanted services have moved to the clouds and dynamically change their IP addresses. But when compiling your own lists of unwanted IP addresses, it will be important for you to know whether the attack continues from the subnet that is important to you. For example, from a public provider network, in which your counterparties may potentially be located.
Plus, through IP you will block addresses that generate alerts in the IDP system.
Why use IDP reports?
The intrusion prevention system is very difficult to set up, because even the best signatures initially give a lot of false positives. At the initial configuration stage, which may take days or even weeks, the ADP report can help to adjust the signatures to your network as much as possible.
Already in operation, the triggered IDP alert probably means the presence of a virus or malware inside the perimeter, and requires the administrator to check the device that caused the alarm. If the system worked on an incoming connection from the outside, then it is most likely just robots looking for open vulnerabilities on servers all over the Internet.
The same graphs, but with a list of top threat sources, are available in the Analytics tab. In addition to IP addresses and hit times, you can see lists of the most frequently visited websites, the most active clients on your network, and the most frequently requested IP addresses. All the same is available for app usage statistics.
Why do I need advanced App Patrol information?
This is a very useful option that will allow you to track the installation of unauthorized software on working computers, as well as predict traffic changes after updating software versions.
In cases where the company is allowed to bring your laptop to the office and work in an isolated network, you will still be able to monitor and block the operation of games, rocking chairs, miners and other unnecessary applications on devices to which you do not have access.
Very useful when setting up filters will be information about the requested domains, both allowed and blocked by the built-in DNS filter. For example, you can see where the telemetry is sent, in what period of time requests were made to which category of servers, and by clicking on any domain, you can see the history of outgoing connections, of course, with a graph of the frequency of requests. If you are interested in the total statistics on traffic and CPU/memory usage, then you need to look at this information directly in the Nebula Control Center, without going to SecuReporter.
Why do I need DNS and URL blocking reports?
Actually, the statistics of domain requests will show which sites are most often visited by employees of your company, and where exactly various network devices are knocking. If you suddenly noticed that after the next update, figuratively speaking, the network printer began knocking on suspicious addresses, perhaps it sends telemetry, which you are not ready for, and it is better to block it.
You may be surprised to find requests to the domain zones of countries with which your company has no relations, especially to the zones .io, .cc, .to and the like. Most likely, this is suspicious software or a virus that should be found and cleaned.
Why do I need information about the work of the antivirus?
If you see constant alarms caused by antivirus in the report, then you need to check computers and any devices from which requests to the network are generated, and if this is a workplace, then have a conversation with an employee about the basics of Internet security, reminding that you cannot open files in emails from strangers, click on suspicious links and go to strange web addresses.
Remember that about 37% of all hacks are carried out using social engineering methods.
Periodic reports by mail
The Secureporter service not only has a beautiful modern dashboard, but also sends a weekly report to the administrator's email about what happened on the network.
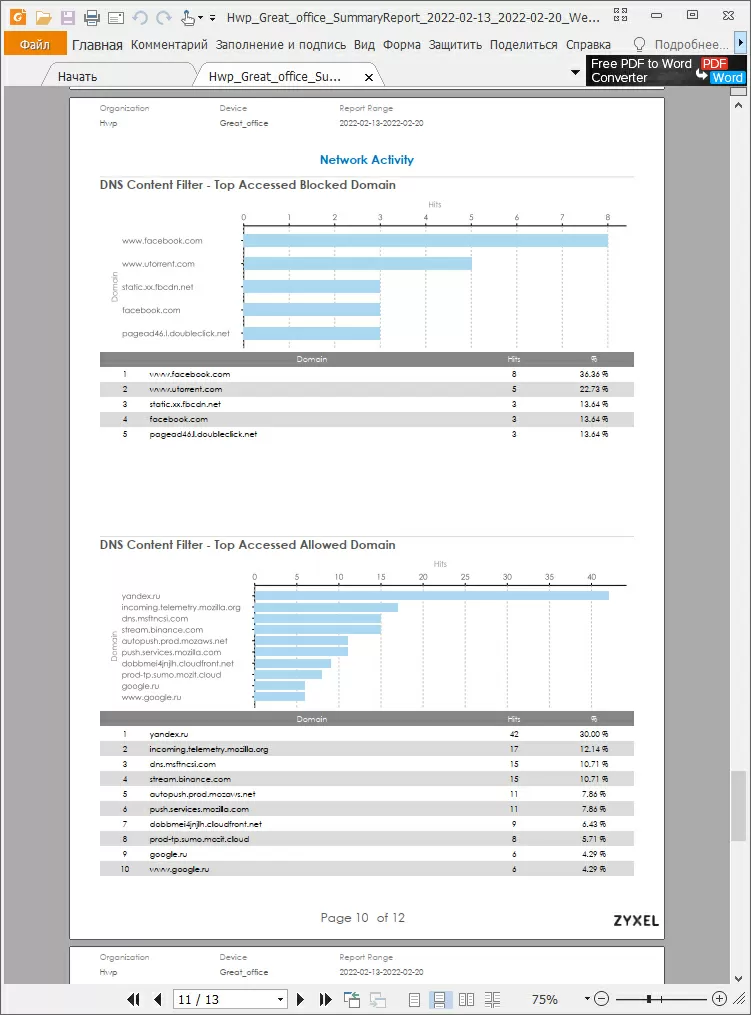
This 13-page report contains all the same information that is available to you on the website, including the most frequently requested addresses and traffic sources. Agree, a printed report is an excellent argument at meetings or other rallies. What a pity that not all services have such a function. In addition, Secureporter informs you about changes in your equipment: if a new Zyxel device has registered on the network or if someone has disconnected the gateway from your organization - in these cases, you will receive an E-Mail notification and you will be able to react.
Conclusions
First of all, SecuReporter is designed for a new generation of administrators who will probably serve the client's network remotely, or have several offices under contract where the network is built on Zyxel equipment. To justify the purchase of a paid subscription to the service, it is enough to know that by adding a gateway to Nebula, you lose access to its Web interface, so you need to somehow track NGFW events. And for everything related to network protection and security, business owners are happy to sign any consumables.
On the other hand, no one forces you to connect the Zyxel gateway to Nebula: you can configure the rules of the built-in services manually, monitor events through the export of logs and connect VPN tunnels with your hands, prescribing router addresses in other filiales. So we can't say that Zyxel is "so-so, extort money for something that should be free." Fortunately, the company always leaves you a choice.
Michael Degtjarev (aka LIKE OFF)
09/03.2022